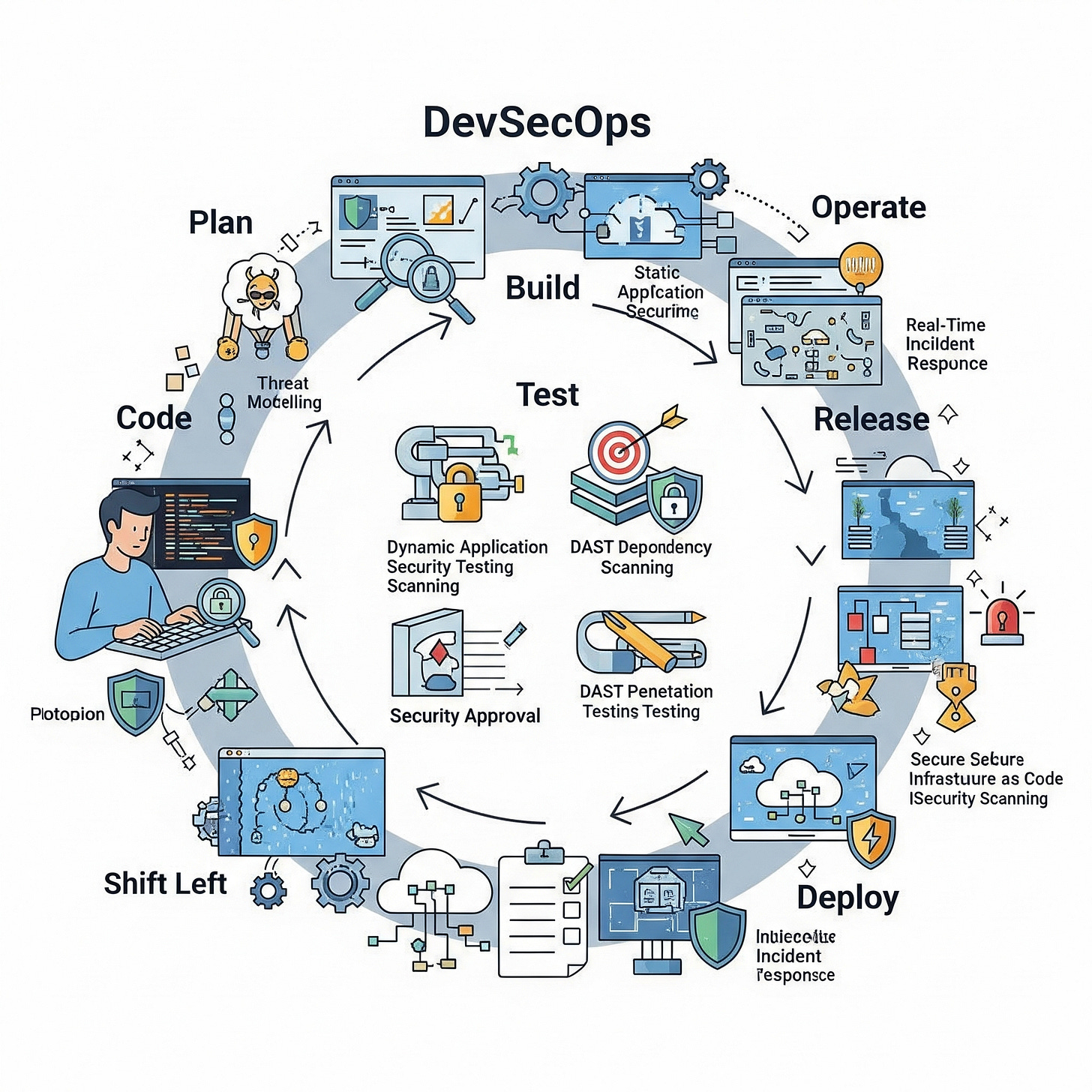
Embed Security into the DevOps Lifecycle (DevSecOps)
"Shift left" to identify and remediate vulnerabilities in code and infrastructure before they reach production.
Last week, we continued our series on 10 Best Cloud Practices for the Modern Enterprise. This week, we will discuss leveraging automation and SOAR capabilities to accelerate response times, reduce human error, and scale security operations.
Software development and continuous deployment are rapidly evolving and changing daily; the most effective and least expensive way to remediate a vulnerability is to prevent it from ever being introduced into a production environment. This is the core principle of DevSecOps, a cultural and technical methodology that "shifts security left" by integrating security practices, tools, and responsibilities directly into the DevOps pipeline.14 Traditionally, security has been an afterthought, a final gate that code must pass through before deployment. This model creates friction, slows down development cycles, and makes remediation far more costly and complex. When a vulnerability is discovered in production, it requires an emergency patch, a full regression testing cycle, and a new deployment, disrupting roadmaps and frustrating developers.
By embedding security into every phase of the Software Development Lifecycle (SDLC)—from coding and building to testing and deployment—organizations can identify and fix vulnerabilities at their source. This proactive approach not only strengthens the security posture of applications and infrastructure but also fosters a culture of shared responsibility for security, breaking down the traditional silos between Development, Security, and Operations teams.
"Shifting Left"
"Shifting left" is the central tenet of DevSecOps. It refers to moving security testing and validation to the earliest possible points in the development pipeline. Instead of security being a final, pre-production check (on the right side of a linear SDLC diagram), it is integrated throughout the process (moving it to the left). This ensures that security is a continuous concern, not a one-time event.
Infrastructure as Code (IaC) Scanning
Modern cloud environments are largely defined by code. Infrastructure as Code (IaC) tools like Azure Resource Manager (ARM) templates, Bicep, and Terraform are used to declaratively define and deploy cloud resources. A critical DevSecOps practice is to scan these IaC templates for security misconfigurations before they are used to provision infrastructure.3 This prevents common security flaws, such as publicly exposed storage accounts or overly permissive network security groups, from ever being created in the cloud environment.
Consider continuously scanning your environment with CrowdStrike, Tenable, Cyvatar.AI or other MSSPs to help ingest your Cloud Vulnerability signals.
Container Image and Software Composition Analysis (SCA)
Applications today are increasingly built from a combination of proprietary code and open-source components, and are often packaged as container images. Two key scanning practices are essential here:
Container Image Scanning: This involves analyzing container images within the CI/CD pipeline for known vulnerabilities in the base operating system and any installed software packages.3 If a vulnerability is found, the build can be failed automatically, preventing the insecure image from being pushed to a registry or deployed.
Software Composition Analysis (SCA): This practice focuses on identifying the open-source libraries and dependencies used in an application and scanning them for known vulnerabilities. Given that open-source components can make up a significant portion of a modern application's codebase, SCA is critical for managing supply chain risk.
Providing Code-to-Cloud Context
A major challenge in DevSecOps is bridging the gap between a developer's view of the code and the security team's view of the production environment. Effective DevSecOps provides developers with "code-to-cloud" context, helping them understand the security implications of their code within the target cloud environment.3 This includes providing clear, actionable remediation guidance directly within their native tools (e.g., their IDE or pull request interface), rather than sending them a separate report from a security tool they don't use.
Microsoft Implementation
Microsoft provides a comprehensive set of tools, integrated into the Defender for Cloud platform, to enable a robust DevSecOps program across multi-cloud and multi-pipeline environments.
Microsoft Defender for Cloud - DevOps Security
DevOps security is a core component of the paid Microsoft Defender CSPM plan and is designed to provide unified security management from code to cloud.4 It offers centralized visibility and control over the security posture of DevOps environments, including native integrations with
Azure DevOps, GitHub, and GitLab.3
Key capabilities of Defender for Cloud's DevOps security solution include:
Unified Visibility: It provides a single dashboard within Defender for Cloud to view the security posture of all connected code repositories, CI/CD pipelines, and development environments. This allows security teams to manage and enforce security policies consistently, regardless of where development is happening.4
IaC and Container Image Scanning: Defender for Cloud integrates directly into CI/CD pipelines to perform automated scanning. It can scan IaC templates (ARM, Bicep, Terraform, CloudFormation) and container images for vulnerabilities and misconfigurations. This can be configured to fail the build if high-severity issues are found, effectively blocking insecure code from being deployed.3
Secrets Scanning: The platform can scan code repositories for exposed secrets, such as API keys, connection strings, and private keys, which are a common source of breaches if accidentally committed to code.
Actionable Remediation Guidance in Developer Workflows: One of the most powerful features is the ability to surface security findings directly within the developer's native workflow. For example, when a developer opens a pull request in Azure DevOps or GitHub, Defender for Cloud can post annotations directly in the PR, highlighting the identified vulnerability and providing clear, code-level remediation guidance.19 This tight feedback loop empowers developers to fix security issues quickly and efficiently, without having to leave their familiar tools.
Code-to-Cloud Context: By correlating findings from the development pipeline with the runtime environment, Defender for Cloud can help prioritize vulnerabilities. For example, it can highlight a vulnerability in a container image that is currently running in a production environment with public internet exposure, providing the full context needed to understand the real-world risk.3
By implementing these capabilities, organizations can move from a high-friction, reactive security model to a seamless, proactive DevSecOps culture. This not only improves security but also accelerates development by reducing the time and cost associated with fixing vulnerabilities late in the lifecycle. The goal is to make security an invisible and invaluable partner in the development process, fostering a culture of shared ownership and continuous improvement.9
Some security tools you can consider for improving your business security posture:
CrowdStrike Falcon: Cybersecurity’s AI-native platform. https://crowdstrike2001.partnerlinks.io/Cpf-coaching
INE Security Awareness and Training https://get.ine.com/cpf-coaching
Tenable vulnerabilities management https://shop.tenable.com/cpf-coaching
Cyvatar.AI Managed endpoint protection solution for SMBs and digital cloud environment https://cyvataraif5706.referralrock.com/l/CHRISTOPHE77/
Omnistruct helping you with your privacy, GRC and security programs. They can act as your BISO to help scale your team and security program https://omnistruct.com/partners/influencers-meet-omnistruct/
Guidde help you turn your tribal and undocumented processes into easy documented videos and instructions https://affiliate.guidde.com/cpf-coaching
Cyberupgrade helps you focus on upgrading your cyber and digital risk because you shouldn’t have to become a compliance expert to grow your business. We handle the complexity of frameworks like DORA, ISO 27001, and NIS2—so your team can stay focused on building, scaling, and serving your customers. https://join.cyberupgrade.net/cpf-coaching
1Password for securing your secrets, tokens, passwords, documents and more, whether you are at home, work or school, they have programs suited for all https://1password.partnerlinks.io/cpf-coaching
Works cited
Vulnerability Management Lifecycle: An Easy Guide - SentinelOne, accessed June 26, 2025, https://www.sentinelone.com/cybersecurity-101/cybersecurity/vulnerability-management-lifecycle/
What is the vulnerability management lifecycle? - Red Canary, accessed June 26, 2025, https://redcanary.com/cybersecurity-101/security-operations/vulnerability-management-lifecycle/
Microsoft Defender for Cloud - CSPM & CWPP | Microsoft Azure, accessed June 26, 2025, https://azure.microsoft.com/en-us/products/defender-for-cloud
Microsoft Defender for Cloud Overview, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/defender-for-cloud/defender-for-cloud-introduction
Start planning multicloud protection in Microsoft Defender for Cloud, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/defender-for-cloud/plan-multicloud-security-get-started
Vulnerability Management Lifecycle: 6 Steps - Swimlane, accessed June 26, 2025, https://swimlane.com/blog/vulnerability-management-lifecycle/
The Vulnerability Management Lifecycle Explained (5 Steps) - PurpleSec, accessed June 26, 2025, https://purplesec.us/learn/vulnerability-management-lifecycle/
The Vulnerability Management Lifecycle in 6 Stages | Wiz, accessed June 26, 2025, https://www.wiz.io/academy/vulnerability-management-lifecycle
Vulnerability Management: Components, Lifecycle & Best Practices ..., accessed June 26, 2025, https://www.exabeam.com/explainers/information-security/vulnerability-management-components-lifecycle-and-best-practices/
Vulnerability Management Framework - Balbix, accessed June 26, 2025, https://www.balbix.com/insights/vulnerability-management-framework/
Vulnerability Management Lifecycle: Key Steps for Security - Akto, accessed June 26, 2025, https://www.akto.io/learn/vulnerability-management-lifecycle
Why Every Vulnerability Management Strategy Starts with Asset Management - SIRP, accessed June 26, 2025, https://sirp.io/blog/why-every-vulnerability-management-strategy-starts-with-asset-management/
Cloud Vulnerability Management [Best Practices 2025] - Sentra, accessed June 26, 2025, https://www.sentra.io/learn/cloud-vulnerability-management
Azure Vulnerability Management Guide for 2025 - SentinelOne, accessed June 26, 2025, https://www.sentinelone.com/cybersecurity-101/cybersecurity/azure-vulnerability-management/
Vulnerability Management Lifecycle: A Comprehensive Guide - Escape.tech, accessed June 26, 2025, https://escape.tech/blog/vulnerability-management-lifecycle/
NIST Vulnerability Management: Defintion and Implementaion, accessed June 26, 2025, https://cynomi.com/nist/nist-vulnerability-management/
NIST CSF 2.0: A Framework for Vulnerability Management - SecurityBridge, accessed June 26, 2025, https://securitybridge.com/blog/nist-csf-2-0-for-vulnerability-management/
The NIST Cybersecurity Framework (CSF) 2.0 - NIST Technical ..., accessed June 26, 2025, https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf
Cloud Security Posture Management (CSPM) - Microsoft Defender for Cloud, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/defender-for-cloud/concept-cloud-security-posture-management
Microsoft Defender Vulnerability Management | Microsoft Security, accessed June 26, 2025, https://www.microsoft.com/en-us/security/business/threat-protection/microsoft-defender-vulnerability-management
Microsoft Defender Vulnerability Management, accessed June 26, 2025, https://learn.microsoft.com/en-us/defender-vulnerability-management/defender-vulnerability-management
Azure Security Control - Vulnerability Management | Microsoft Learn, accessed June 26, 2025, https://learn.microsoft.com/en-us/security/benchmark/azure/security-control-vulnerability-management
Vulnerability Management Best Practices - PurpleSec, accessed June 26, 2025, https://purplesec.us/learn/vulnerability-management-best-practices/
Overview - Data security posture management - Microsoft Defender for Cloud, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/defender-for-cloud/concept-data-security-posture
PowerBI Dashboard - SQL Queries - Rapid7 Discuss, accessed June 26, 2025, https://discuss.rapid7.com/t/powerbi-dashboard/41520
Microsoft Defender for Cloud - CSPM & CWPP | Microsoft Azure, accessed June 26, 2025, https://azure.microsoft.com/en-us/products/defender-for-cloud/
Connect your AWS account - Microsoft Defender for Cloud ..., accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/defender-for-cloud/quickstart-onboard-aws
Steps to Integrate Microsoft Defender for Cloud with AWS Account — Enable Defender for Servers | by Poojashetty | KPMG UK Engineering | Medium, accessed June 26, 2025, https://medium.com/kpmg-uk-engineering/steps-to-integrate-microsoft-defender-for-cloud-with-aws-account-enable-defender-for-servers-b2110d6be0f6
Protect your Amazon Web Services (AWS) containers with Defender for Containers, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/defender-for-cloud/tutorial-enable-container-aws
Microsoft Security for AWS - Azure Architecture Center, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/architecture/guide/aws/aws-azure-security-solutions
Enable Defender for open-source relational databases on AWS (Preview) - Learn Microsoft, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/defender-for-cloud/enable-defender-for-databases-aws
Connect your GCP project - Microsoft Defender for Cloud | Microsoft ..., accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/defender-for-cloud/quickstart-onboard-gcp
Protect your Google Cloud Platform (GCP) containers with Defender for Containers, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/defender-for-cloud/tutorial-enable-container-gcp
Defender For Vulnerability Management - Microsoft Security, accessed June 26, 2025, https://secureazcloud.com/f/defenderforvulneralibilitymanagement
Vulnerability Management Resources - SANS Institute, accessed June 26, 2025, https://www.sans.org/blog/vulnerability-management-resources/
Beyond CVSS: Smarter Vulnerability Prioritization with Exploit Data ..., accessed June 26, 2025, https://www.recastsoftware.com/resources/beyond-cvss-smarter-vulnerability-prioritization/
Strategic Recommendation for Transitioning from CVSS to Risk-Based Vulnerability Prioritization - Netpoleon Solutions, accessed June 26, 2025, https://www.netpoleons.com/blog/strategic-recommendation-for-transitioning-from-cvss-to-risk-based-vulnerability-prioritization
Risk-Based Vulnerability Management: Prioritize What Matters | Wiz, accessed June 26, 2025, https://www.wiz.io/academy/risk-based-vulnerability-management
What is Vulnerability Prioritization? And how to do it right - JAMF Software, accessed June 26, 2025, https://www.jamf.com/blog/vulnerability-prioritization-guide-for-it-experts/
CVSS 4.0 and Beyond: A Context-Aware Approach to Vulnerability ..., accessed June 26, 2025, https://www.armis.com/blog/cvss-4-0-and-beyond-a-context-aware-approach-to-vulnerability-risk-assessment/
What Is Vulnerability Prioritization? Strategies and Steps - Legit Security, accessed June 26, 2025, https://www.legitsecurity.com/aspm-knowledge-base/vulnerability-prioritization
What Is Vulnerability Prioritization? - Picus Security, accessed June 26, 2025, https://www.picussecurity.com/resource/glossary/what-is-vulnerability-prioritization
NIST SP 800-53r5 Compliance Guide | Vulnerability Management Best Practices - Brinqa, accessed June 26, 2025, https://www.brinqa.com/blog/nist-800-53-vulnerability-management/
Vulnerabilities by ACR - Tenable documentation, accessed June 26, 2025, https://docs.tenable.com/cyber-exposure-studies/application-software-security/Content/VulnerabilitiesACR.htm
Risk Prioritization - Tenable documentation, accessed June 26, 2025, https://docs.tenable.com/cyber-exposure-studies/cyber-exposure-insurance/Content/RiskPrioritization.htm
Discover Your Most Critical Assets Before Hackers Do | HackerNoon, accessed June 26, 2025, https://hackernoon.com/discover-your-most-critical-assets-before-hackers-do
What is Vulnerability Prioritization? | Bitsight, accessed June 26, 2025, https://www.bitsight.com/learn/vulnerability-prioritization
Vulnerability Assessment Report: A C-Suite Guide — KEYCALIBER, accessed June 26, 2025, https://www.keycaliber.com/resources/-vulnerability-assessment-report-a-c-suite-guide
Why Vulnerability Assessment Reports Fail (& How To Fix It) - PurpleSec, accessed June 26, 2025, https://purplesec.us/learn/vulnerability-assessment-reporting/
Why an IAM Assessment is Crucial for Your Cybersecurity Strategy, accessed June 26, 2025, https://www.identityfusion.com/blog/why-an-iam-assessment-is-crucial-for-your-cybersecurity-strategy
What is Identity Access Management (IAM)? - CrowdStrike, accessed June 26, 2025, https://www.crowdstrike.com/en-us/cybersecurity-101/identity-protection/identity-access-management-iam/
The Role of IAM in Preventing Cyber Attacks - Infisign, accessed June 26, 2025, https://www.infisign.ai/blog/the-role-of-iam-in-preventing-cyber-attacks
The Importance of Identity and Access Management in Safeguarding Your Enterprise, accessed June 26, 2025, https://www.infosecurity-magazine.com/blogs/identity-access-management/
What is Privileged Identity Management? - Microsoft Entra ID ..., accessed June 26, 2025, https://learn.microsoft.com/en-us/entra/id-governance/privileged-identity-management/pim-configure
Microsoft Security - Privileged Identity Management (PIM), accessed June 26, 2025, https://www.microsoft.com/en-us/security/business/identity-access/microsoft-entra-privileged-identity-management-pim
Microsoft Entra Conditional Access | Microsoft Security, accessed June 26, 2025, https://www.microsoft.com/en-us/security/business/identity-access/microsoft-entra-conditional-access
Configure Microsoft Entra for increased security (Preview), accessed June 26, 2025, https://learn.microsoft.com/en-us/entra/fundamentals/configure-security
Microsoft Entra ID (formerly Azure Active Directory) | Microsoft Security, accessed June 26, 2025, https://www.microsoft.com/en-us/security/business/identity-access/microsoft-entra-id
Learn about privileged access management | Microsoft Learn, accessed June 26, 2025, https://learn.microsoft.com/en-us/purview/privileged-access-management
Beware the Hidden Risk in Your Entra Environment - The Hacker News, accessed June 26, 2025, https://thehackernews.com/2025/06/beware-hidden-risk-in-your-entra.html
Microsoft nOAuth Flaw Still Exposes SaaS Apps Two Years After Discovery, accessed June 26, 2025, https://www.infosecurity-magazine.com/news/microsoft-noauth-flaw-2025/
What is Automated Vulnerability Remediation? - SentinelOne, accessed June 26, 2025, https://www.sentinelone.com/cybersecurity-101/cybersecurity/what-is-automated-vulnerability-remediation/
What Is Automated Vulnerability Remediation? | Benefits & Best Practices for Security Teams - Brinqa, accessed June 26, 2025, https://www.brinqa.com/blog/automated-vulnerability-remediation/
Automate Threat Response with Playbooks in Microsoft Sentinel ..., accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/sentinel/automation/automate-responses-with-playbooks
Vulnerability Management Automation: Here's Why You Need it - Swimlane, accessed June 26, 2025, https://swimlane.com/blog/automating-vulnerability-lifecycle-management/
Vulnerability Management in Microsoft Azure - NubOps, accessed June 26, 2025, https://www.nubops.com/blog/2024/02/22/vulnerabilities/
Automating Threat Detection and Response with Microsoft Sentinel Playbooks - ne Digital, accessed June 26, 2025, https://www.nedigital.com/en/blog/automating-threat-detection-and-response-with-microsoft-sentinel-playbooks
Automation in Microsoft Sentinel, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/sentinel/automation/automation
Automate threat response with playbooks in Microsoft Sentinel - GitHub, accessed June 26, 2025, https://github.com/MicrosoftDocs/azure-docs/blob/main/articles/sentinel/automation/automate-responses-with-playbooks.md
Azure Logic Apps | Microsoft Azure, accessed June 26, 2025, https://azure.microsoft.com/en-us/products/logic-apps
Overview - Azure Logic Apps | Microsoft Learn, accessed June 26, 2025, https://learn.microsoft.com/en-us/azure/logic-apps/logic-apps-overview
Automated remediation in Azure - Netskope Community, accessed June 26, 2025, https://community.netskope.com/security-posture-management-4/automated-remediation-in-azure-5876
Mastering SANS Vulnerability Management: A Comprehensive Guide - Astra Security, accessed June 26, 2025, https://www.getastra.com/blog/compliance/sans/sans-vulnerability-management/
Vulnerability Management Policy: 3 Examples and 6 Best Practices | Sternum IoT, accessed June 26, 2025, https://sternumiot.com/iot-blog/vulnerability-management-policy-3-examples-and-6-best-practices/
Best Practices for SLA Vulnerability Management - FortifyFramework.com, accessed June 26, 2025, https://www.fortifyframework.com/sla-vulnerability-management/
Nucleus Blog | Adapt Vulnerability Management Service Level ..., accessed June 26, 2025, https://nucleussec.com/blog/how-to-adapt-vulnerability-management-service-level-agreements-to-team-maturity/
How Soon Should Vulnerabilities Be Patched? - Tandem, accessed June 26, 2025, https://tandem.app/blog/how-soon-should-vulnerabilities-be-patched
Vulnerability Management SLAs: A Guide - HostedScan.com, accessed June 26, 2025, https://hostedscan.com/blog/vulnerability-management-slas-guide
Vulnerability Remediation | safecomputing.umich.edu, accessed June 26, 2025, https://safecomputing.umich.edu/protect-the-u/protect-your-unit/vulnerability-management/remediation
FortifyData's Alignment with NIST SP 800-40, accessed June 26, 2025, https://fortifydata.com/blog/fortifydata-alignment-with-nist-sp-800-40/
Microsoft Defender Vulnerability Management Plans and Pricing, accessed June 26, 2025, https://www.microsoft.com/en-us/security/business/threat-protection/microsoft-defender-vulnerability-management-pricing
Top 10 Vulnerability Management Metrics & KPIs To Measure Success, accessed June 26, 2025, https://purplesec.us/learn/vulnerability-management-metrics/
15 Vulnerability Management Metrics to Measure your Program - Wiz, accessed June 26, 2025, https://www.wiz.io/academy/vulnerability-management-metrics
Vulnerability Management Reports | Rootshell Security, accessed June 26, 2025, https://www.rootshellsecurity.net/vulnerability-management-reports/
Using the SANS Vulnerability Management Maturity Model in Your Vulnerability Management Process - RH-ISAC, accessed June 26, 2025, https://rhisac.org/vulnerability-management/sans-maturity-model-process/
15 Key Vulnerability Management Metrics for Success - Legit Security, accessed June 26, 2025, https://www.legitsecurity.com/aspm-knowledge-base/top-vulnerability-management-metrics
Vulnerability Management Metrics: 5 Metrics to Start Measuring in ..., accessed June 26, 2025, https://www.sans.org/blog/5-metrics-start-measuring-vulnerability-management-program/
Automated Remediation: Benefits, Best Practices & Use Cases - Tamnoon, accessed June 26, 2025, https://tamnoon.io/blog/automated-cloud-remediation-guide/
How to report on vulnerability management to the board - Intruder.io, accessed June 26, 2025, https://www.intruder.io/blog/reporting-to-the-board-how-to-talk-about-vulnerability-management
Vulnerability Dashboard using Microsrft Power BI - YouTube, accessed June 26, 2025,
How to Create a Custom Security & Threat Dashboard in Power BI, accessed June 26, 2025, https://www.techrepublic.com/article/how-to-visualise-security-and-threat-information-in-power-bi/
RAPID 7 as a source for Vulnerabilities dashboard - Microsoft Fabric Community, accessed June 26, 2025, https://community.powerbi.com/t5/Desktop/RAPID-7-as-a-source-for-Vulnerabilities-dashboard/td-p/2284223