Security Copilot in Microsoft 365 E5: Maximizing AI-Powered Security Capabilities
Discover how Security Copilot in Microsoft 365 E5 can help you unlock the full potential of AI-powered security features, empowering your organization to stay protected and ahead of emerging threats.
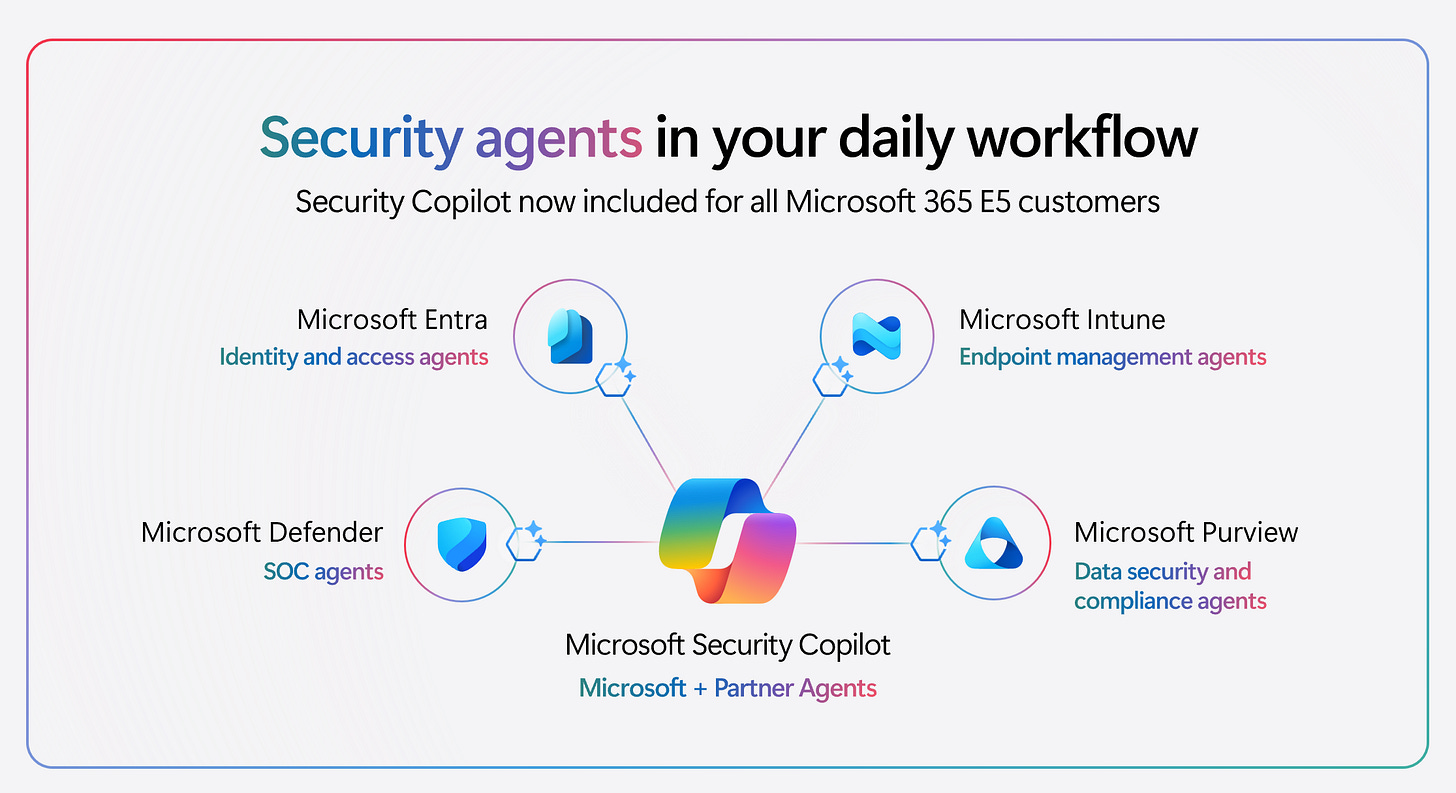
Microsoft’s recent Ignite 2025 announcements mark a paradigm shift in enterprise security. Microsoft Security Copilot, the AI-powered security assistant, is now included with Microsoft 365 E5 licenses at no additional cost. This means organizations with E5 subscriptions gain built-in access to intelligent security “copilots” across the Microsoft ecosystem, from threat protection in Defender to identity management in Entra. In practical terms, a mid-sized enterprise (for example, 500 E5 users) will now automatically receive about 200 Security Copilot compute units per month included in their license, sufficient for typical interactive AI security scenarios, without any extra spend. [learn.microsoft.com], [robquickenden.blog] [learn.microsoft.com]