Strengthening Your Digital Defense: Practical Cybersecurity Approaches for SMB Tech Executives in 2025
The cyber environment presents ongoing challenges with rising cyber threats, and Small to Medium Businesses (SMBs) often find themselves particularly at risk. Although high-profile breaches frequently make the news, SMBs are sometimes targeted because they’re seen as more vulnerable and have limited resources, making them what some might call "low-hanging fruit" for cybercriminals.
The mind map below illustrates the many considerations regarding this topic.
The stark reality for SMBs is alarming. A staggering 76% of SMBs experienced a ransomware attack in the last year, a rate that outpaces larger enterprises. This is not merely an inconvenience; for many, it presents an existential threat, with one in four small businesses reportedly "one disaster or threat away from shutting down". The average breach cost for an SMB stands at a significant $25,000, underscoring the severe financial repercussions. This numerical disparity reveals a critical systemic vulnerability. Larger organizations typically possess extensive security budgets, dedicated teams, and sophisticated infrastructure. In contrast, SMBs, operating with "far less resources", are not only being targeted more frequently but are also likely to experience a disproportionately higher impact from each attack. This means cybersecurity for SMBs must be framed as a fundamental business continuity and survival issue, not merely an optional IT expense. The advice must be highly tailored to their resource constraints, emphasizing maximum impact for minimal investment, and demonstrating that the cost of inaction far outweighs the cost of proactive measures.
Despite this critical need, most SMB leaders struggle to prioritize cybersecurity due to tight budgets and limited resources. There is a clear misalignment between recognizing the need for improvement (59% of respondents) and the actual intent to invest (only 49%). This report aims to bridge that gap, offering practical, cost-effective, and integrated solutions to build robust cybersecurity resilience.
The Evolving Threat Actors: Why SMBs Can't Afford to Wait
The world of cybersecurity is ever-changing, and it's fascinating to see how threats keep evolving along with it. The AI boom of 2024 is now delivering on its "promises made by both vendors and bad actors" in 2025. This translates to increasingly sophisticated, AI-augmented attacks, including "highly adaptive malware and phishing campaigns that evolve in real time to bypass traditional defenses". Corporate executives are already facing "highly personalized, sophisticated phishing scams, likely powered by AI to enhance attack precision and effectiveness". Since over 90% of successful cyberattacks originate from phishing emails, traditional methods like endpoint security and standard email filters are no longer sufficient. AI's dual role in offensive and defensive cybersecurity means a rapid escalation of capabilities on both sides, making traditional, static defenses increasingly irrelevant. The adoption of AI by attackers necessitates a corresponding, if not superior, adoption of AI in defense. This means SMBs must understand that their historical security approaches are becoming obsolete. Investing in AI-driven security tools, such as Managed Detection and Response (MDR) or Extended Detection and Response (XDR), is no longer a luxury but a strategic necessity to effectively counter the evolving, AI-powered threats.
Ransomware continues to be a dominant threat, evolving in severity and frequency. SMBs remain a prime target, often seen as "low-hanging fruit" due to their limited budgets and security resources. The financial and operational disruption caused by ransomware can be devastating, directly contributing to the risk of business closure.
A significant and growing concern is ransomware attacks targeting software supply chains, with 91% of organizations expressing concern about attacks on their "downstream software supply chain, third-party and connected partners". This trend is particularly critical for SMBs, which frequently rely on a smaller network of managed service providers (MSPs) and third-party platforms, inadvertently increasing their exposure to these complex supply chain threats. This highlights a critical shift in the attack surface. A breach is no longer confined to an organization's direct perimeter but can originate from any trusted vendor or partner. An SMB's security posture is inherently tied to the cybersecurity hygiene of its entire ecosystem. This necessitates a broader security strategy for SMBs that extends beyond internal systems. It emphasizes the importance of rigorous vendor risk assessment, due diligence, and the application of Zero Trust principles to all third-party interactions, effectively treating external partners as extensions of their security perimeter. This implies a need for robust contract clauses and continuous monitoring of vendor security practices.
Foundational Pillars: Building a Resilient Security Posture
Zero Trust frameworks are transitioning from aspirational concepts to "essential" requirements for SMBs in 2025 as threats evolve. This principle, based on "never trust, always verify," significantly reduces vulnerabilities and minimizes the impact of attacks. A practical, cost-effective starting point for SMBs involves securing identities through Multi-Factor Authentication (MFA) and role-based access controls. Beyond identity, it extends to ensuring endpoint protection with antivirus and device management tools, segmenting networks to limit potential breaches, and implementing tools to detect and respond to threats.
Comprehensive IT Asset Management (ITAM) is not merely an administrative task but a critical cybersecurity enabler. It provides "crystal-clear visibility over your global assets," allowing businesses to know "exactly what you've got and where they are". This visibility is crucial for identifying vulnerable assets and bolstering their defenses. Effective ITAM streamlines processes, reduces manual errors that can lead to costly mistakes and security risks, and ensures compliance. It helps answer critical questions like "What operating systems are our laptops running?" and "Which devices are vulnerable to the latest threats?". Manual and administrative tasks and limited visibility in IT asset management directly lead to "costly mistakes" and put "IT infrastructure at risk," opening up "security risks". Robust ITAM, in contrast, significantly improves cybersecurity resilience and helps identify vulnerable assets. This establishes a clear, direct relationship: a lack of proper ITAM creates significant security vulnerabilities, whereas robust ITAM is a prerequisite for effective cybersecurity. An organization cannot secure what it does not know or control.
Traditional defenses are no longer sufficient against sophisticated, AI-augmented attacks. SMBs must adopt a layered defense strategy that pairs foundational frameworks like Zero Trust with advanced technologies. AI-powered Managed Detection and Response (MDR) solutions, for instance, offer continuous threat hunting and monitoring, enabling real-time attack identification and significantly reducing vulnerability to modern threats. Extended Detection and Response (XDR) solutions, such as Microsoft 365 Defender, unify protection, detection, and response across endpoints, identities, email, and applications, automating actions to disrupt in-progress attacks and self-heal affected systems.
Actionable Steps for SMB Tech Leaders: Your Cybersecurity Playbook
Step 1: Gain Unparalleled Visibility with Smart IT Asset Management
An organization cannot protect what it does not know exists. A robust IT Asset Management (ITAM) strategy provides the foundational visibility essential for cybersecurity. This means identifying, categorizing, and continuously monitoring all IT assets, from physical devices to software licenses and cloud instances.
Manual ITAM tasks are prone to "costly mistakes" and create "information silos". Leveraging automated asset detection tools is crucial for SMBs with limited staff. These tools can automatically update asset records, track device health, and even set up geofences to prevent loss. This continuous discovery process should detect all approved and unapproved assets and collect granular details like installed software and running services. For SMBs, the initial investment in automated ITAM tools, even cost-effective ones, yields significant return by reducing operational overhead, minimizing human error, and providing continuous, real-time security visibility that would otherwise be impossible with limited staff. This makes advanced ITAM capabilities accessible and practical for businesses that cannot afford large IT teams.
It is also vital to manage the entire asset lifecycle, from procurement to deployment, maintenance, and secure disposal. This includes regular maintenance checks to extend the lifespan and prevent costly repairs.
For SMBs utilizing cloud environments, tools like Azure Resource Graph (ARG) offer powerful, scalable resource exploration. ARG allows querying Azure infrastructure for details like VM sizes, storage configurations, and network settings. Combined with Azure Arc, it can even provide server inventory management across hybrid multi-cloud and on-premises environments from a single pane of glass. This helps identify unmanaged or misconfigured resources, a critical security blind spot.
While comprehensive ITAM best practices and policy components can appear daunting, small businesses can reduce expenses, prevent unnecessary asset replacements, and improve operational efficiency by implementing simple asset tracking and maintenance strategies. The availability of free or cost-effective ITAM tools suggests that SMBs do not need to implement an enterprise-grade solution simultaneously. By breaking down ITAM into manageable, incremental steps, SMBs can achieve significant security and operational benefits without overwhelming their limited resources. This approach makes the seemingly daunting task of comprehensive ITAM manageable and impactful from day one, fostering continuous improvement rather than aiming for immediate, unachievable perfection.
The following table outlines cost-effective ITAM tools and their key features for SMBs:
Step 2: Fortify Your Identity Perimeter with Multi-Factor Authentication and Conditional Access
Multi-Factor Authentication (MFA) is a cornerstone of Zero Trust, ensuring "only verified users and compliant devices can access resources". Since over 90% of successful cyberattacks stem from phishing, MFA significantly mitigates this primary attack vector. It should be mandatory for all users, especially those with administrative roles. Modern security extends beyond an organization's network perimeter to include user and device identity, positioning identity as the new control plane. Investing in and properly configuring identity and access management solutions like Microsoft Entra ID is paramount. It offers a robust, integrated, and scalable way to control who accesses what, from where, and under what conditions, significantly reducing the attack surface. This foundational, high-return security measure provides robust protection against a wide array of modern cyber threats, particularly those targeting user credentials.
Microsoft Entra Conditional Access acts as a "Zero Trust policy engine," making access decisions based on various signals: user identity, device security, location, application sensitivity, and real-time risk detection. This allows for granular control, such as blocking access from specific untrusted locations or requiring MFA when users are off the corporate network.
Implementing Conditional Access for SMBs using Microsoft Entra ID involves several practical steps. First, ensure the Microsoft 365 tenant has the necessary Entra ID Premium P2 licenses (e.g., via Microsoft 365 E5 or E5 Security add-on) and assign appropriate administrator roles, such as Security Administrator or Conditional Access Administrator. Before deploying new policies, reviewing existing risk reports (e.g., Risky Users, Risky Sign-ins) in the Entra admin center is critical to understand the current security posture and address any immediate high-risk accounts. Communication about policy changes to users helps manage expectations and reduces potential friction. Crucially, designated "emergency access" or "break-glass" accounts are excluded from strict MFA or risk policies to prevent accidental lockouts. Also, consider excluding service accounts or legacy systems if they cannot use modern authentication methods. When configuring policies, MFA is required for all cloud resource users. Define "Named locations" for trusted IP ranges (e.g., the corporate office network) to create more nuanced policies, such as allowing access without MFA from trusted locations but requiring it from untrusted ones. Finally, always deploy new Conditional Access policies in "Report-only" mode first to assess their impact without enforcing them, allowing for fine-tuning settings and avoiding disruptions.
Step 3: Proactive Threat Detection, Vulnerability Management, and Incident Response
A continuous, automated workflow for asset discovery, vulnerability management, threat prioritization, and remediation is essential. This includes continuously checking all assets—on-premises, public clouds, and endpoints—for vulnerabilities and misconfigurations using active scans and lightweight agents. Prioritize remediation efforts by focusing on the "riskiest vulnerabilities on the most critical assets," often leveraging machine learning and threat intelligence. This emphasis on "proactive response" and "early threat detection" is a key aspect of modern security. Automated asset discovery and the use of machine learning to identify severe vulnerabilities, coupled with centralized patch management, represent a fundamental shift from a reactive "clean up after the breach" mentality to a proactive "prevent the breach" strategy. This automated, intelligent approach is critical for SMBs, who are often "strapped for time and resources" and prone to "costly mistakes" from manual tasks. Modern security is about preventing attacks before they cause damage. Automated and intelligent systems allow SMBs to gain a proactive stance, continuously monitoring and identifying risks, which is far more efficient and effective than constantly playing catch-up after an incident occurs. This reinforces the value of AI in defense and provides a clear path for SMBs to maximize their limited security resources.
Timely patching is a critical component of breach prevention. Centralize, consolidate, and automate patch management processes to ensure uniformity and efficiency, preventing delays that can lead to breaches.
Even with robust preventative measures, the possibility of an attack remains. NIST asset management advocates for creating clear "incident response and recovery strategies to mitigate such risk impact". A well-maintained asset inventory becomes invaluable during an incident, providing immediate context about the attack's nature and timeline, enabling faster investigation and response. Proactive response involves early threat detection to identify risks before they escalate. The detailed asset inventory provided by ITAM is the essential input for effective vulnerability detection and prioritization (VMDR). When an incident occurs, this comprehensive, up-to-date asset data provides critical context, allowing faster and more effective response and recovery. Strong ITAM enables efficient VMDR, and both are indispensable for a robust incident response capability. SMBs must view these security functions as deeply interconnected and mutually reinforcing elements of a holistic security program. Investing in one area, such as improving ITAM visibility, directly enhances the effectiveness and efficiency of others, like vulnerability management and incident response. This integrated perspective helps SMBs optimize their limited resources by building a cohesive and resilient security posture, rather than treating security components in silos.
Step 4: Secure Your Cloud and Endpoints
For SMBs leveraging cloud services, managing security posture is paramount. Solutions like Microsoft Defender for Cloud provide "unified visibility into your cloud security posture across Azure, AWS, Google Cloud, and hybrid clouds". It continuously assesses resources for misconfigurations and vulnerabilities, offering actionable recommendations. This includes identifying unauthenticated, inactive, or externally exposed APIs. Cloud Security Posture Management (CSPM) also integrates security into DevOps workflows by scanning Infrastructure-as-Code (IaC) templates and container images early in the development lifecycle, preventing misconfigurations from reaching production ("shift-left security"). Microsoft Defender for Cloud's CSPM capabilities are heavily focused on "strengthening the overall security posture," identifying "weak spots," and flagging "misconfigurations" and "vulnerabilities early in the SDLC". This proactive approach, which aims to prevent issues from reaching production, is a significant departure from traditional reactive security. By proactively managing and hardening the security posture, SMBs can significantly reduce their attack surface and the likelihood of a successful breach, minimizing the need for costly and disruptive incident response. SMBs should prioritize tools and strategies that enable continuous security posture management. This means actively hardening their cloud environments, identifying and remediating misconfigurations, and reducing their attack surface, rather than solely relying on detection after an attack has begun. This proactive approach is more efficient and cost-effective for resource-constrained businesses, as it prevents problems rather than just reacting to them.
Beyond traditional antivirus, SMBs need comprehensive endpoint protection. This involves deploying Endpoint Protection Platforms (EPP) and Endpoint Detection and Response (EDR) solutions. Microsoft Defender for Endpoint, for instance, uses behavioral sensors, cloud security analytics, and threat intelligence to provide next-generation protection, attack surface reduction, and automated investigation and remediation. Ransomware protection is a key component here.
Step 5: Cultivate a Security-First Culture and Strategic Partnerships
Human error remains a significant vulnerability. "Lack of awareness leads to misuse and security gaps". It is essential to educate employees on ITAM best practices regularly, enforce IT usage policies, and implement comprehensive security awareness training. Clear communication about new security measures, such as the implementation of Conditional Access policies, helps reduce confusion and support calls, fostering user adoption rather than resistance. Even the most sophisticated technical controls and automated systems can be undermined by human error, negligence, or a lack of understanding. Informed and disciplined employees become an active layer of defense, maximizing the effectiveness of technological investments. Cybersecurity is a shared responsibility across the entire organization, not solely the domain of the IT department. SMBs must invest in technology, continuous security awareness training, and developing clear, actionable policies that guide employee behavior. Empowering employees with knowledge and clear guidelines transforms them from potential vulnerabilities into an active and crucial line of defense, significantly enhancing the overall security posture and maximizing the return on investment of other security measures.
With the rise of supply chain attacks, SMBs must "assess vendors more closely for risk". This means understanding the security posture of Managed Service Providers (MSPs) and any third-party platforms relied upon. Streamlining the security stack by choosing integrated solutions (like the Microsoft ecosystem, which offers unified XDR and SIEM capabilities) can reduce complexity, minimize exposure, and simplify security management for resource-constrained teams.
Maximizing Your Cybersecurity Investment: The ROI of Resilience
While budget constraints are a primary concern for SMBs, viewing cybersecurity purely as a cost center is a critical oversight. There is a fundamental paradox where SMB leaders recognize a vital need to improve cybersecurity (59% agree). Still, a significant portion (only 49%) do not intend to invest, primarily due to budget concerns. This is not just about a lack of funds; it is a strategic misalignment where short-term financial pressures are prioritized over potentially catastrophic long-term risks. The average breach cost of $25,000, and the fact that one in four SMBs are at risk of shutting down, highlights that a perceived high investment cost leads to underinvestment, increasing the likelihood and severity of breaches, ultimately resulting in far greater actual costs. Cybersecurity spending must be framed not as a discretionary IT expense but as a necessary business investment that protects revenue, reputation, and operational continuity.
Effective asset management and robust cybersecurity measures translate directly into tangible business benefits, offering a compelling return on investment (ROI). The "cost of inaction" is demonstrably higher than the "cost of investment". SMBs must understand that "saving money" on cybersecurity is a false economy that exposes them to catastrophic risks. Proactive investment in cybersecurity is a form of essential risk mitigation that ultimately preserves capital, ensures business longevity, and protects the business's hard-earned reputation.
The tangible benefits of a strong cybersecurity posture include:
Reduced Costs: Proactive security prevents costly breaches, which average $25,000 per incident. ITAM helps extend asset lifespans, reduces redundant purchases, and reduces waste. Centralized patch management reduces delays and associated costs.
Improved Operational Efficiency: Direct outcomes include streamlining maintenance workflows, reducing downtime through preventive measures, and optimizing asset utilization. Automated ITAM reduces manual administrative tasks and errors.
Enhanced Productivity: Minimized disruptions from cyber incidents or equipment failures lead to uninterrupted productivity for employees.
Streamlined Compliance: ITAM keeps licenses and warranties up-to-date, reducing the risk of penalties and ensuring adherence to security and legal standards. NIST asset management helps achieve compliance and provides auditors with detailed system information. Defender for Cloud continuously assesses against regulatory standards like PCI-DSS and HIPAA.
Support for Scalable Growth: A well-managed IT infrastructure and robust security posture enable businesses to scale seamlessly, accommodating new employees, offices, and tools without unnecessary complexity or security debt. ITAM, in particular, contributes to "operational efficiency, cost-effectiveness, and sustainable growth," driving business growth through maximizing asset utilization, predictable budgeting, reducing downtime, and supporting scalable growth. This positions ITAM as a strategic business investment that directly contributes to the bottom line and future growth, rather than being perceived solely as a cybersecurity or IT expense. ITAM provides the stable, secure foundation for an SMB to expand confidently and efficiently by optimizing resource allocation, reducing downtime, and ensuring compliance.
Improved Decision-Making: Real-time data from ITAM and CSPM provides insights into asset performance, vulnerabilities, and potential attack paths, allowing for data-driven decisions on investments and remediation.
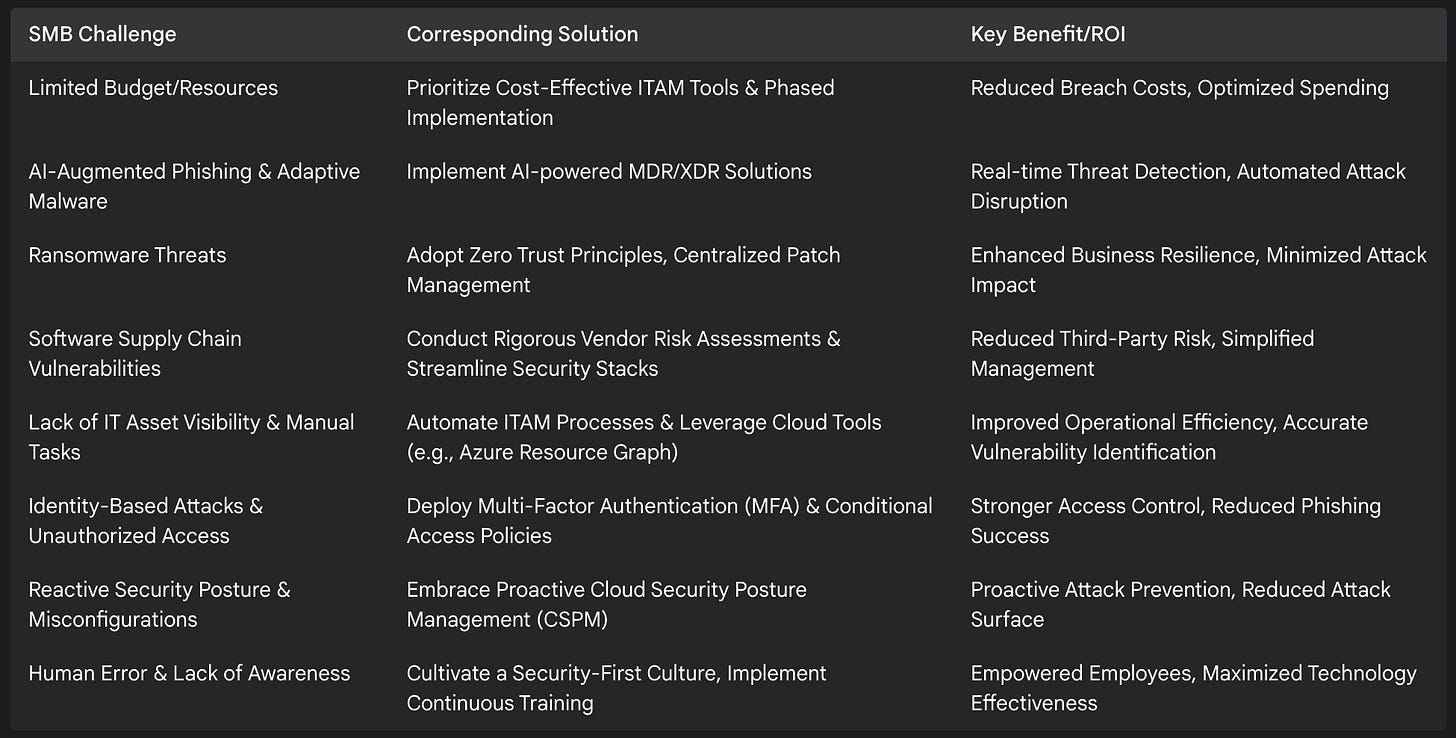
The following table summarizes key cybersecurity challenges for SMBs and their corresponding solutions:
Conclusion: Building a Resilient Future, Together
For SMBs, it is undoubtedly challenging yet manageable with a proactive, layered defense strategy. The importance of Zero Trust, comprehensive IT Asset Management, and modern, AI-driven security solutions cannot be overstated. Resource-constrained businesses can establish a strong security posture by prioritizing high-impact, cost-effective measures and fostering a security-first culture. The journey to resilience is ongoing, and each step taken today strengthens tomorrow's digital frontier. Cybersecurity is not just an IT burden but a strategic investment in a business's longevity, growth, and reputation. Tech and cyber leaders within SMBs are urged to take decisive action, shifting their security posture from reactive to proactive, resilient defense.
SMB partners I would recommend provide managed security services and solutions, whether you have five or more than 20 stakeholders.
Cyvatar AI https://cyvataraif5706.referralrock.com/l/CHRISTOPHE77/
Need help with your Risk Management and Governance services? Reach out to
Omnistruct https://omnistruct.com/partners/influencers-meet-omnistruct/