The Phantom Workforce: A Guide to Combating State-Sponsored IT Infiltration
Uncover the secrets of fighting state-sponsored IT infiltration
The global shift to remote work has created a new, insidious threat: state-sponsored IT workers infiltrating companies to generate illicit revenue and steal intellectual property. A highly sophisticated campaign by North Korea is exploiting the vulnerabilities of remote hiring, placing fraudulent IT workers inside businesses ranging from startups to Fortune 500 corporations. This isn't just fraud; it's a national security issue, with the U.S. Department of Justice confirming these schemes are designed to evade sanctions and fund the North Korean regime's weapons programs.
These operatives are not lone wolves. They are part of an industrialized deception campaign, tracked by Microsoft as "Jasper Sleet," that has grown in scale and sophistication. Understanding their playbook is the first step to building a defense.
Anatomy of a Deception Campaign
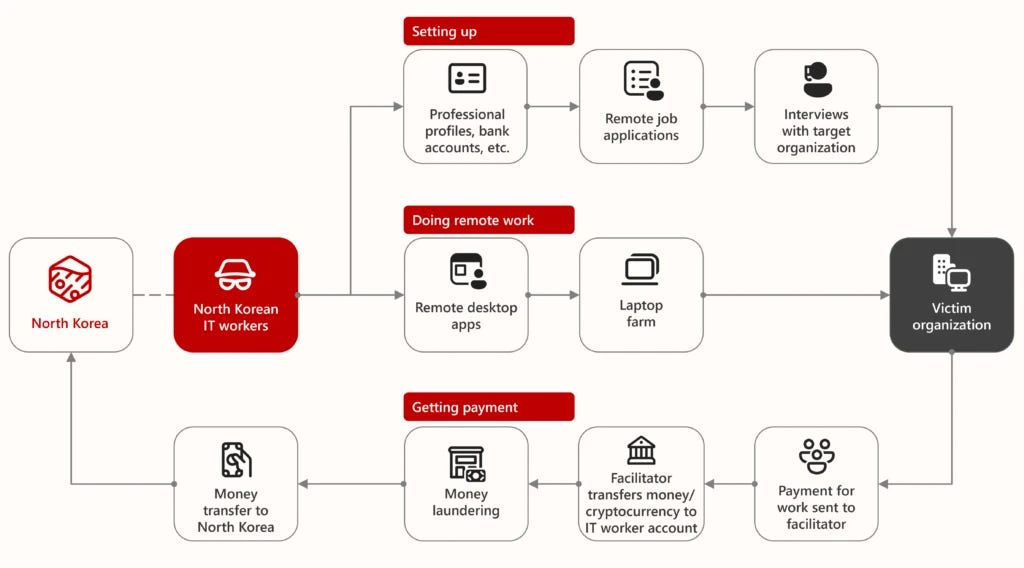
The North Korean infiltration strategy is a multi-stage operation designed to create the perfect phantom employee :
Identity Laundering: The process begins by stealing or "renting" the identities of real U.S. persons. Operatives then use AI tools to enhance their own photos and forge identity documents, creating polished, professional-looking resumes that are often free of the grammatical errors that once served as a red flag.
Digital Persona Crafting: They build a believable digital footprint for these fake personas, creating profiles on professional networking sites and developer platforms to showcase fabricated portfolios.
Evasion and Impersonation: To hide their true locations in North Korea, China, or Russia, they use a layered infrastructure of VPNs and proxy services. During interviews, they frequently make excuses to keep their cameras off and have been observed using voice-changing software.
The "Laptop Farm" Network: A critical component is the network of U.S.-based facilitators who operate "laptop farms." These individuals receive company-issued laptops, allowing the overseas operatives to remotely access them. This makes all their network traffic appear to originate from a legitimate U.S. IP address on a trusted company device, bypassing basic security controls.
Once inside, these operatives pose a dual threat. They generate income for the DPRK and act as pre-positioned insider threats, capable of stealing priceless intellectual property, source code, and sensitive data.
Fortifying the Human Perimeter: A New Hiring Framework
Defeating a threat that exploits human trust requires reinforcing the human-centric processes of hiring and onboarding.
1. Rethink the Remote Interview The interview must evolve from a simple skills assessment into an identity verification event.
Mandatory Live Video: A strict, non-negotiable policy requiring all interviews to be conducted over a live video feed is the first line of defense. Excuses about "technical issues" with a camera should be treated as a major red flag.
Active On-Camera ID Check: Ask the candidate to hold their government-issued photo ID up to the camera for a live visual comparison.
Proactive Deepfake Detection: Train interviewers to spot the signs of deepfakes. Ask the candidate to perform unpredictable actions, like turning their head slowly to one side or briefly covering their face with their hand. Real-time deepfakes often struggle to render these movements accurately, which can cause visible distortions or artifacts.
2. High-Assurance Onboarding The onboarding process is the final and most critical gateway. It must create an unbreakable link between the digital persona and a legal, physical identity.
Automated Digital Identity Proofing: Before granting any access, mandate that the candidate completes a verification process with a reputable third-party Identity Verification (IDV) provider like Onfido, Veriff, or Jumio. These services use AI to authenticate government-issued IDs and perform a biometric comparison between the ID photo and a live selfie, including a "liveness" check to prevent spoofing.
Secure Device Provisioning: Ship company hardware exclusively to the verified home address established during the IDV process. To disrupt interception, consider sending the laptop and critical credentials (like a hardware security key) separately.
Implementing a Zero Trust Architecture for Continuous Verification
Robust hiring procedures are essential, but the long-term security of the organization depends on a technical architecture that assumes a breach is inevitable. This is the core principle of Zero Trust: never trust, always verify. This model discards the outdated "castle-and-moat" approach, where anything inside the network is trusted. In a Zero Trust Architecture (ZTA), every request to access a resource is treated as if it comes from an untrusted network and must be explicitly verified.
Identity as the New Perimeter: In a ZTA, security is built around identity, not network location. Access is granted based on a dynamic assessment of the user, their device health, and other contextual signals. This directly counters the North Korean tactic of using U.S.-based laptop farms to appear "trusted".
Least Privilege Access: Users are granted only the minimum level of access required to do their job. This is critical for damage control. If a fraudulent worker is hired, their ability to move laterally across the network and access sensitive data is severely limited, containing the "blast radius" of the infiltration.
Continuous Monitoring: Trust is not a one-time event at login. A ZTA continuously monitors user and device behavior, looking for anomalies. If a user's risk score suddenly spikes, the system can automatically trigger a re-authentication challenge or revoke access entirely.
The Technology Stack for Zero Trust
Major cloud providers offer the core building blocks for a ZTA.
Microsoft: The ecosystem is centered on Microsoft Entra ID (formerly Azure AD).
Conditional Access acts as the policy engine, using signals like user risk, device compliance, and location to enforce access rules.
Continuous Access Evaluation (CAE) takes this further by revoking access in near real-time if a critical event occurs, like a user's account being disabled or their IP address suddenly changing to an untrusted location.
Google Cloud: Google's BeyondCorp model is the embodiment of Zero Trust. It uses
Cloud Identity as the identity store and the Identity-Aware Proxy (IAP) as the enforcement gateway. IAP sits in front of applications, verifying every user and device before allowing access, making applications invisible to the public internet.
Amazon Web Services (AWS): Security is managed through AWS IAM Identity Center, which centralizes access management across multiple AWS accounts. It relies heavily on temporary credentials and "permission sets" to enforce least-privilege, just-in-time access, a core tenet of Zero Trust.
Conclusion
The phantom workforce threat is a patient, well-resourced national security operation targeting the private sector. Defeating it requires a unified strategy that combines fortified HR procedures with a resilient Zero Trust security architecture. By hardening the human perimeter with rigorous identity verification and implementing a technical framework that continuously verifies every access request, organizations can protect their assets and avoid becoming unwilling accomplices in a global security threat.
Some security tools you can consider for improving your business security posture:
CrowdStrike Falcon: Cybersecurity’s AI-native platform. https://crowdstrike2001.partnerlinks.io/Cpf-coaching
INE Security Awareness and Training https://get.ine.com/cpf-coaching
Tenable vulnerabilities management https://shop.tenable.com/cpf-coaching
Cyvatar.AI Managed endpoint protection solution for SMBs and digital cloud environment https://cyvataraif5706.referralrock.com/l/CHRISTOPHE77/
Omnistruct helping you with your privacy, GRC and security programs. They can act as your BISO to help scale your team and security program https://omnistruct.com/partners/influencers-meet-omnistruct/
Guidde help you turn your tribal and undocumented processes into easy documented videos and instructions https://affiliate.guidde.com/cpf-coaching
Cyberupgrade helps you focus on upgrading your cyber and digital risk because you shouldn’t have to become a compliance expert to grow your business. We handle the complexity of frameworks like DORA, ISO 27001, and NIS2—so your team can stay focused on building, scaling, and serving your customers. https://join.cyberupgrade.net/cpf-coaching
1Password for securing your secrets, tokens, passwords, documents and more, whether you are at home, work or school, they have programs suited for all https://1password.partnerlinks.io/cpf-coaching
Works Cited
https://www.onblick.com/blogs/remote-i-9-completion-9-best-practices-for-employers
https://www.paloaltonetworks.com/cyberpedia/what-is-beyondcorp
https://www.hrcloud.com/blog/secure-onboarding-best-practices-for-protecting-data-with-remote-hires
https://pilotcore.io/blog/zero-trust-and-remote-work-enhancing-security-in-a-remote-workforce
https://www.reddit.com/r/googlecloud/comments/ll4frz/gcp_beyondcorp_zero_trust/
https://www.daon.com/resource/how-identity-verification-can-make-remote-work-more-secure/
https://www.crowdstrike.com/en-us/cybersecurity-101/zero-trust-security/
https://www.paloaltonetworks.com/cyberpedia/what-is-a-zero-trust-architecture
https://www.microsoft.com/en-us/security/business/secure-remote-work
https://www.cisa.gov/topics/physical-security/insider-threat-mitigation
https://www.turing.ac.uk/blog/what-are-deepfakes-and-how-can-we-detect-them
https://learn.microsoft.com/en-us/azure/active-directory-b2c/partner-onfido
https://www.cyber.gc.ca/en/guidance/zero-trust-approach-security-architecture-itsm10008
https://learn.microsoft.com/en-us/entra/verified-id/plan-verification-solution
https://www.sailpoint.com/identity-library/10-tips-for-onboarding-remote-employees
https://learn.microsoft.com/en-us/entra/identity/conditional-access/overview
https://learn.microsoft.com/en-us/entra/identity/authentication/overview-authentication
https://www.cbsnews.com/news/north-korea-duping-us-companies-tech-worker-scheme-doj/
https://staffbase.com/blog/remote-onboarding-the-new-employee-experience/
https://www.zscaler.com/resources/security-terms-glossary/what-is-zero-trust-architecture
https://hyperspace.mv/i-9-verification-during-remote-onboarding/
https://www.accusourcehr.com/blog/mitigating-hiring-risks-in-the-remote-work-era-1
https://www.authx.com/blog/verifying-identity-remote-workforce/
https://www.meritalk.com/articles/doj-disrupts-north-korean-remote-it-worker-fraud-schemes/
https://www.newsweek.com/north-korea-it-remote-worker-american-charged-scheme-2092759
https://blog.knowbe4.com/tips-for-detecting-real-time-deepfakes-a-guide-to-staying-one-step-ahead
https://learn.microsoft.com/en-us/entra/identity/authentication/how-to-enable-passkey-fido2
https://www.apono.io/blog/iam-identity-center-the-essential-guide-to-aws-identity-center/
https://learn.microsoft.com/en-us/entra/verified-id/partner-gallery
https://www.apnews.com/article/fbi-justice-department-north-korea-c65e175c6ccd722e691d56121dff9e5e
https://www.meegle.com/en_us/topics/deepfake-detection/deepfake-detection-for-interviews
https://www.realitydefender.com/insights/detect-deepfake-job-interviews
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_providers_saml_3rd-party.html
https://jumpcloud.com/support/integrate-with-aws-iam-identity-center
https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-identity.html
https://console.cloud.google.com/marketplace/details/google-cloud-platform/customer-identity
https://cloud.google.com/identity-platform/docs/concepts-authentication
https://documentation.onfido.com/getting-started/general-introduction
https://docs.aws.amazon.com/cognito/latest/developerguide/what-is-amazon-cognito.html
https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pools-identity-provider.html
https://aws.amazon.com/marketplace/seller-profile?id=80df1302-6aff-4906-b60f-29952164f8b4
https://www.getfocal.ai/blog/best-identity-verification-software-solutions
https://docs.aws.amazon.com/cognito/latest/developerguide/identity-pools.html
https://console.cloud.google.com/marketplace/product/google-cloud-platform/customer-identity