Two CISOs Talking Cyber Podcast - Zero Trust Security: Least Privilege
and I discussed the first tenet of Zero Trust Architecture in today’s podcast. I will include additional resources and references for those looking to go deeper down the Rabbit Hole.Previous blogs on the topic from me:
NIST SP 800-207 https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf
Summary:
Understanding the principle of Least Privilege is essential for enhancing cybersecurity within an organization. Here's a breakdown of the minimum pros, cons, opportunities, and challenges associated with its use:
Pros:
Enhanced Security: By limiting access rights for users to the bare minimum necessary to perform their tasks, the principle of Least Privilege reduces the potential attack surface for cybercriminals.
Reduced Insider Threats: It minimizes the risk of insider threats, whether intentional or accidental, by restricting access to sensitive information and critical systems.
Easier Compliance: Helps organizations comply with regulatory standards and privacy laws by demonstrating that access controls are in place and that data exposure is minimized.
Cons:
Implementation Complexity: Setting up Least Privilege access can be complex and time-consuming, requiring a detailed understanding of every user's role and responsibilities.
Potential Productivity Impact: If not managed properly, it could lead to situations where employees are unable to access necessary resources promptly, affecting productivity.
Ongoing Management: Requires continuous monitoring and adjustment as roles change within an organization, adding to administrative overhead.
Opportunities:
Improved Security Posture: Implementing Least Privilege can significantly enhance an organization's overall security posture, making it more resilient to attacks.
Cost Savings: By reducing the risk of data breaches, organizations can save on the costs associated with cyber incidents, including fines, remediation efforts, and reputational damage.
Adaptability to Cloud Environments: As more organizations move to cloud-based services, Least Privilege can be efficiently implemented to manage access in these dynamic environments.
Challenges:
Determining Access Levels: Accurately defining the access levels required for each user or system can be challenging, especially in complex environments with many interdependent systems and applications.
Resistance from Users: Users accustomed to having broad access may resist the imposition of more restrictive controls, perceiving it as a loss of autonomy or trust.
Keeping Policies Up-to-Date: As organizations evolve, keeping access privileges aligned with current roles and responsibilities requires ongoing vigilance and effort.
Incorporating Least Privilege within an organization's security framework presents a balanced set of pros and cons. While it significantly enhances security and compliance, it demands careful planning and continuous management. However, the opportunities it presents for improving an organization's security posture and reducing the risk of data breaches are compelling reasons to overcome these challenges.







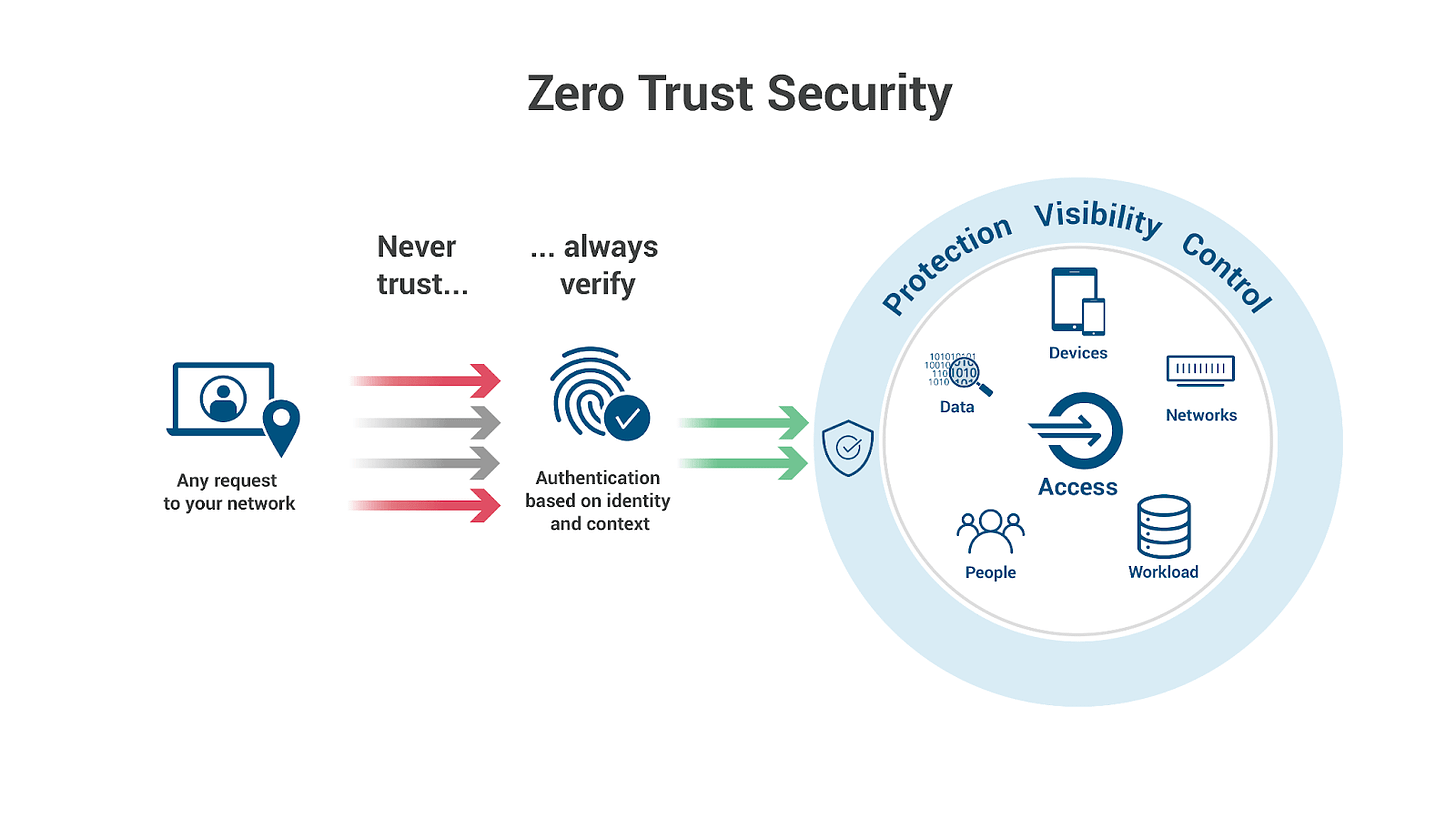









Two CISOs Talking Cyber Podcast - Zero Trust Security: Least Privilege