Digital Supply Chain Risks: Understanding, Identifying, and Mitigating Vulnerabilities
Explore the significance of understanding digital supply chain risks in today's cloud-centric and globalized environment. Delve into the potential gaps, threats, and mitigation strategies to fortify.
Bottom Line Up Front:
Understanding your digital supply chain risk is becoming one of the significant challenges many businesses face today, especially with the move to the cloud and the globalization of the computing behind those services. Recommendations on addressing the additional detailing of the supply chain, which might be part of any significant applications
Ensure that COTS/Third Party Suppliers/SaaS are documented on the security context diagram, threat model, CMDB, and any other sources of record, as well as potential platforms that might support them as part of their digital supply chain.
Ensuring that these dependencies are captured will help to identify supply chain risks better, threat model potential mitigations for them, as well as a myriad of other detection and response activities.
Overview of Supply Chain Risk
An organization’s understanding of the supply chain risk of any given system can vary based on the number of integrators or suppliers a company might use to generate its revenue through the production of software or delivery of services, in addition to understanding those integrators or suppliers, understanding the external factors that might affect them and, in turn, affect the producer.
An organization’s ability to identify, detect, and respond to environmental threats/influences to the supply chain becomes critical in maintaining software and services' integrity. An organization’s Third Party Management (TPM) program helps monitor its Third Parties. This program also helps with the lifecycle management of suppliers while servicing the Organization.
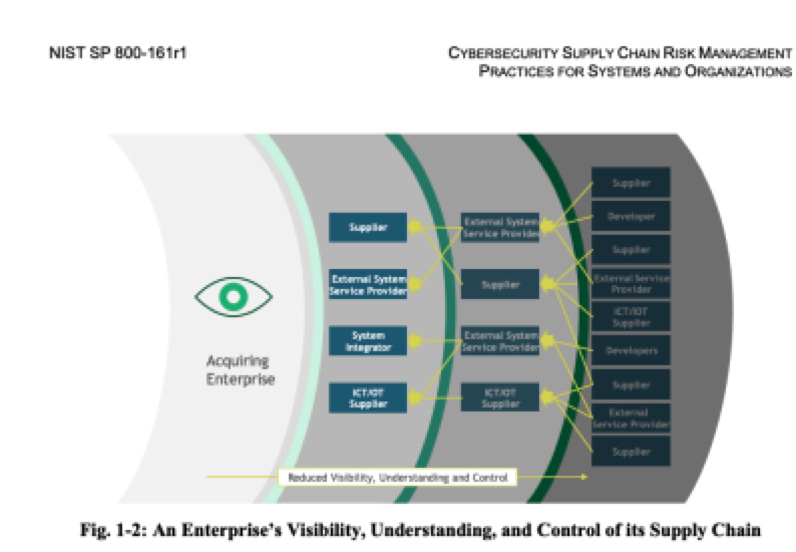
Due to the complexity of an organization’s supply chain, there might be multiple layers of suppliers or intermediaries downstream. As the layers of downstream suppliers increase, the Organization’s ability to have visibility into those suppliers decreases. The figure below from NIST SP 800–161r1 demonstrates the decreased invisibility as the layers of the supply chain increase.
1 NIST SP 800–161r1 Fig. 1–2 An Enterprise’s Visibility, Understanding, and Control of its Supply Chain https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-161r1.pdf
This paper will focus on the digital supply chain risks that affect Organizations.
Potential Gaps in Organization Digital Supply Chain
Organizations use a layered approach of controls and processes that manage their digital supply chain; this first section will focus on the internal management of the production of applications and services.
Gaps in Cyber Architecture Requirements
Organizations might not document or track 3rd Parties/Supplier Chain infrastructure as part of its supply chain in its Change Management Database (CMDB), which is not required to be completed.
Impact (So What?):
This means that the Organization might not be able to proactively respond to significant vulnerabilities in our supply chain, which have been integrated or used to build the organization’s products. (e.g., Log4J)
Potential Mitigation:
We can understand the technologies used to support solutions by our critical suppliers and have them linked as an artifact in CMDB and TPM. This will provide the Organization with the ability to proactively understand the risk exposure from suppliers, as demonstrated in the figure below. 2