Develop and Enforce Robust Remediation Policies and SLAs
Establish clear policies, roles, responsibilities, and timelines to ensure accountability and drive timely remediation.
Last week, we continued our series on 10 Best Cloud Practices for the Modern Enterprise. This week, we will focus on creating and implementing effective Remediation Policies and SLAs. It is essential to establish clear policies, roles, responsibilities, and timelines that ensure accountability and facilitate prompt remediation.
To move a vulnerability management program from an informal, ad-hoc effort to a mature, predictable, and auditable business function, organizations must establish and enforce formal policies and Service Level Agreements (SLAs). A well-defined vulnerability management policy serves as the authoritative document that outlines the organization's commitment to security, establishes clear processes, and defines roles and responsibilities.73 SLAs, in turn, translate the policy's goals into concrete, measurable, and time-bound objectives for remediation.75
Without these formal structures, remediation efforts often lack consistency, accountability, and urgency. Responsibilities can become blurred, critical vulnerabilities may linger for extended periods, and it becomes impossible to measure the effectiveness of the program. A robust policy and enforceable SLAs are essential for standardizing the security response, ensuring compliance with industry regulations and customer commitments, and providing a clear framework for holding teams accountable for timely risk reduction.
Key Components of a Vulnerability Management Policy
A comprehensive vulnerability management policy should be a formal, approved document that is accessible to all relevant stakeholders. While the specifics will vary based on the organization, a strong policy, aligned with frameworks like those from SANS, should include the following key components 73:
Policy Overview, Scope, and Objectives: This section clearly states the purpose of the policy, the assets and environments it covers (e.g., all cloud and on-premises production systems), and the high-level goals it aims to achieve, such as reducing the risk of data breaches and ensuring regulatory compliance.
Roles and Responsibilities: This is a critical section that explicitly assigns ownership for each part of the vulnerability management lifecycle. It should define the responsibilities of the security team (e.g., for scanning and prioritization), IT operations and DevOps teams (e.g., for testing and deploying patches), and asset/business owners (e.g., for accepting risk and approving exceptions).
Vulnerability Management Process: The policy should codify the lifecycle stages discussed in Section 1. It should detail the required processes for asset discovery, scanning frequency, risk assessment methodology, remediation procedures, and verification testing.
Reporting and Remediation (SLAs): This section details the communication plan for vulnerability findings and formally defines the remediation timelines (SLAs) based on risk or severity level.
Exceptions Process: No policy can cover every scenario. This section must outline a formal process for requesting, approving, and documenting exceptions. An exception might be needed if a patch would break a critical business application or if a vulnerability exists in an end-of-life system where no patch is available.73 The process should require justification, compensating controls, and periodic review.
Defining and Benchmarking Remediation SLAs
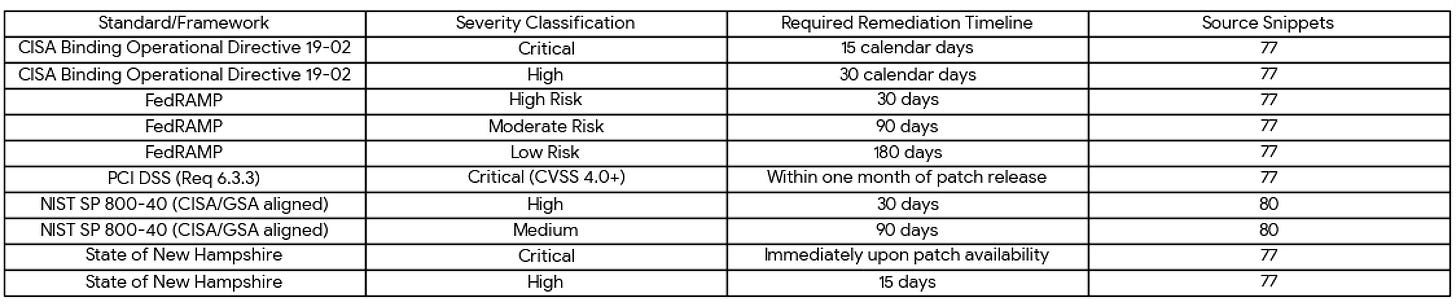
SLAs are the teeth of the vulnerability management policy. They are formal agreements that define the maximum allowable time to remediate a vulnerability once it has been identified and prioritized.76 These timelines are typically stratified by severity level. While every organization must define SLAs that align with its own risk tolerance, it is a best practice to benchmark them against established industry standards and regulatory requirements. This provides a defensible and auditable basis for the policy.
The following table provides a comparative analysis of remediation timelines from several prominent standards, offering a valuable starting point for organizations developing their own SLAs.
Note: Some standards may have slight variations in their definitions or timelines. For example, some sources indicate a 60-day timeline for FedRAMP Moderate risk vulnerabilities.77 Organizations should always refer to the latest official documentation for the specific standards they must comply with.
A common challenge with rigid, one-size-fits-all SLAs is that they can create friction and may not be practical for all teams or asset types.77 For example, a legacy application with a complex, manual testing process may not be able to meet the same aggressive SLA as a standard Windows server managed by an automated patching system. Therefore, a mature approach involves evolving from a simple, universal SLA to a more nuanced, contextual model as the program matures.76 This could involve creating different SLAs for different environments (e.g., production vs. development) or incorporating risk factors into the timeline. For example, a mature SLA might state: "All critical vulnerabilities on internet-facing, production assets with a known public exploit must be remediated within 7 days," while a less urgent critical vulnerability might have a 30-day timeline.76 This adaptive approach aligns the policy with the operational realities of the business and fosters a more collaborative relationship between security and IT teams.
Some security tools you can consider for improving your business security posture:
CrowdStrike Falcon: Cybersecurity’s AI-native platform. https://crowdstrike2001.partnerlinks.io/Cpf-coaching
INE Security Awareness and Training https://get.ine.com/cpf-coaching
Tenable vulnerabilities management https://shop.tenable.com/cpf-coaching
Cyvatar.AI Managed endpoint protection solution for SMBs and digital cloud environment https://cyvataraif5706.referralrock.com/l/CHRISTOPHE77/
Omnistruct helping you with your privacy, GRC and security programs. They can act as your BISO to help scale your team and security program https://omnistruct.com/partners/influencers-meet-omnistruct/
Guidde help you turn your tribal and undocumented processes into easy documented videos and instructions https://affiliate.guidde.com/cpf-coaching
Cyberupgrade helps you focus on upgrading your cyber and digital risk because you shouldn’t have to become a compliance expert to grow your business. We handle the complexity of frameworks like DORA, ISO 27001, and NIS2—so your team can stay focused on building, scaling, and serving your customers. https://join.cyberupgrade.net/cpf-coaching
1Password for securing your secrets, tokens, passwords, documents and more, whether you are at home, work or school, they have programs suited for all https://1password.partnerlinks.io/cpf-coaching
Works Cited:
Mastering SANS Vulnerability Management: A Comprehensive Guide - Astra Security, accessed June 26, 2025, https://www.getastra.com/blog/compliance/sans/sans-vulnerability-management/
Vulnerability Management Policy: 3 Examples and 6 Best Practices | Sternum IoT, accessed June 26, 2025, https://sternumiot.com/iot-blog/vulnerability-management-policy-3-examples-and-6-best-practices/
Best Practices for SLA Vulnerability Management - FortifyFramework.com, accessed June 26, 2025, https://www.fortifyframework.com/sla-vulnerability-management/
Nucleus Blog | Adapt Vulnerability Management Service Level ..., accessed June 26, 2025, https://nucleussec.com/blog/how-to-adapt-vulnerability-management-service-level-agreements-to-team-maturity/
How Soon Should Vulnerabilities Be Patched? - Tandem, accessed June 26, 2025, https://tandem.app/blog/how-soon-should-vulnerabilities-be-patched
Vulnerability Management SLAs: A Guide - HostedScan.com, accessed June 26, 2025, https://hostedscan.com/blog/vulnerability-management-slas-guide
Vulnerability Remediation | safecomputing.umich.edu, accessed June 26, 2025, https://safecomputing.umich.edu/protect-the-u/protect-your-unit/vulnerability-management/remediation
FortifyData's Alignment with NIST SP 800-40, accessed June 26, 2025, https://fortifydata.com/blog/fortifydata-alignment-with-nist-sp-800-40/